UK Data Breach Response Plan Guide
A data breach response plan is, in essence, your organisation's playbook for when things go wrong. It's a documented strategy that outlines exactly what your business will do the moment a security incident is suspected or confirmed. The goal is to move fast and in a coordinated way, limiting the fallout – whether that’s financial loss, operational chaos, or a damaged reputation. With the average cost of a data breach now running into the millions, having a clear, actionable plan isn't just good practice; it's a critical part of business survival for professional services firms.
First Steps When You Suspect a Data Breach
That gut-wrenching moment you realise you might have a breach is where chaos can easily take hold. What you do in those first few hours is absolutely critical. It can dramatically change the outcome of the entire situation, from how well you contain the problem to whether you stay on the right side of regulators. Acting quickly and methodically isn't just a suggestion; it’s a requirement under UK GDPR.

This initial phase isn’t about fixing everything at once. It’s about stabilising the situation, stopping it from getting worse, and setting the stage for a proper investigation. Every move you make has to be done with one eye on preserving evidence.
Activate Your Response Team Immediately
The very first thing you do is get your incident response team in motion. This is not the time to be figuring out who needs to be involved. Your data breach response plan should already have this laid out: the roles, the responsibilities, and the contact details for your core team.
Consider a London-based accountancy firm that discovers an employee has clicked a sophisticated phishing link, potentially exposing its entire client database. The IT manager spots unusual network traffic and immediately triggers the plan. This action instantly pulls the Managing Partner, Legal Counsel, and Head of IT into a secure communication channel to start coordinating their next steps.
In the midst of a crisis, clarity is your greatest asset. Knowing exactly who to call and what their role is prevents the fatal hesitation that allows a minor incident to escalate into a major disaster.
Getting everyone together in that initial huddle is crucial. It establishes who's leading the response and ensures everyone understands the severity of what's happening. It also stops different departments from going off and doing their own thing, which could mean one team accidentally deletes the very evidence another team needs.
Establish Secure Out-of-Band Communications
If you suspect your corporate network is compromised, the last thing you should do is use your usual communication tools. Your company email or internal messaging system could easily be monitored by the attackers, giving them a front-row seat to your response strategy.
Your next move has to be switching all incident-related communications to a secure, separate channel. This could be:
- A pre-arranged, encrypted messaging group on an app like Signal.
- A conference call bridge hosted by a trusted third party.
- Personal email addresses, though this is really a last-ditch, less secure option.
Our London accountancy firm, for example, immediately moves all conversations to a dedicated Signal group. This keeps their discussions about containment, legal duties, and initial findings completely confidential and out of sight of the potential intruder. It's a simple step, but it denies the attacker crucial intelligence and gives your team the freedom to operate.
Begin Initial Assessment and Containment
With the team assembled and communicating securely, the focus shifts. You need to get a handle on the scope of the incident without trampling all over the digital crime scene. The aim is to contain the threat while preserving evidence for the forensic investigation that will inevitably follow.
The firm’s IT team starts by taking the affected employee's laptop off the network. This stops any potential malware from spreading further. Crucially, they don’t just wipe the machine clean, as that would destroy vital evidence. At the same time, they're digging into network logs to figure out the scale of the data exfiltration and what specific parts of the client database were accessed.
This dual approach of containment and assessment is vital. You're trying to stop the bleeding while simultaneously understanding the nature of the wound. The decisive actions you take in these first few hours will set the tone for everything that comes after, from notifying the ICO to eventually recovering and learning from the incident.
Assembling Your Data Breach Response Team
When a data breach hits, the last thing you want is confusion. Who’s in charge? Who calls the lawyers? Who tells the clients? A well-defined incident response plan is useless without the right people to bring it to life. Putting together a dedicated response team beforehand means that when the pressure is on, you have a coordinated, efficient group ready to act, not a panicked scramble.
Think of this as your crisis A-Team. It’s a cross-functional group of specialists pulled from different parts of your business, each with a clear role. Without this structure, crucial tasks get missed, response times drag on, and the damage from the breach multiplies.
Defining Your Key Internal Roles
The heart of your response will always be your internal team. These are the people who know your systems, your culture, and your business inside and out, giving them the context to make smart decisions quickly. This isn't just about job titles; it's about assigning clear, practical responsibilities.
- The Incident Lead: This is your quarterback. They direct the entire response, coordinate every moving part, and act as the single point of contact for senior leadership. In a professional services firm, this is often a Senior Partner or the Head of Operations. Their job is to maintain a bird's-eye view and keep the entire operation on track.
- The IT Security Team: These are your digital first responders. They dive straight into the technical mess to investigate the breach, figure out how far it's spread, and work on containing the threat. They’re the detectives piecing together the what, how, and when of the attack so you can shut it down.
- Legal Counsel: In the UK, this role is absolutely critical. Your legal expert is there to guide you through the maze of GDPR and ICO reporting obligations. They advise on liability, ensure all your actions are legally defensible, and make sure any evidence collected will actually stand up if needed later.
Understanding where threats come from helps illustrate why a skilled IT team is so vital. They need to be able to interpret alerts from all kinds of sources.
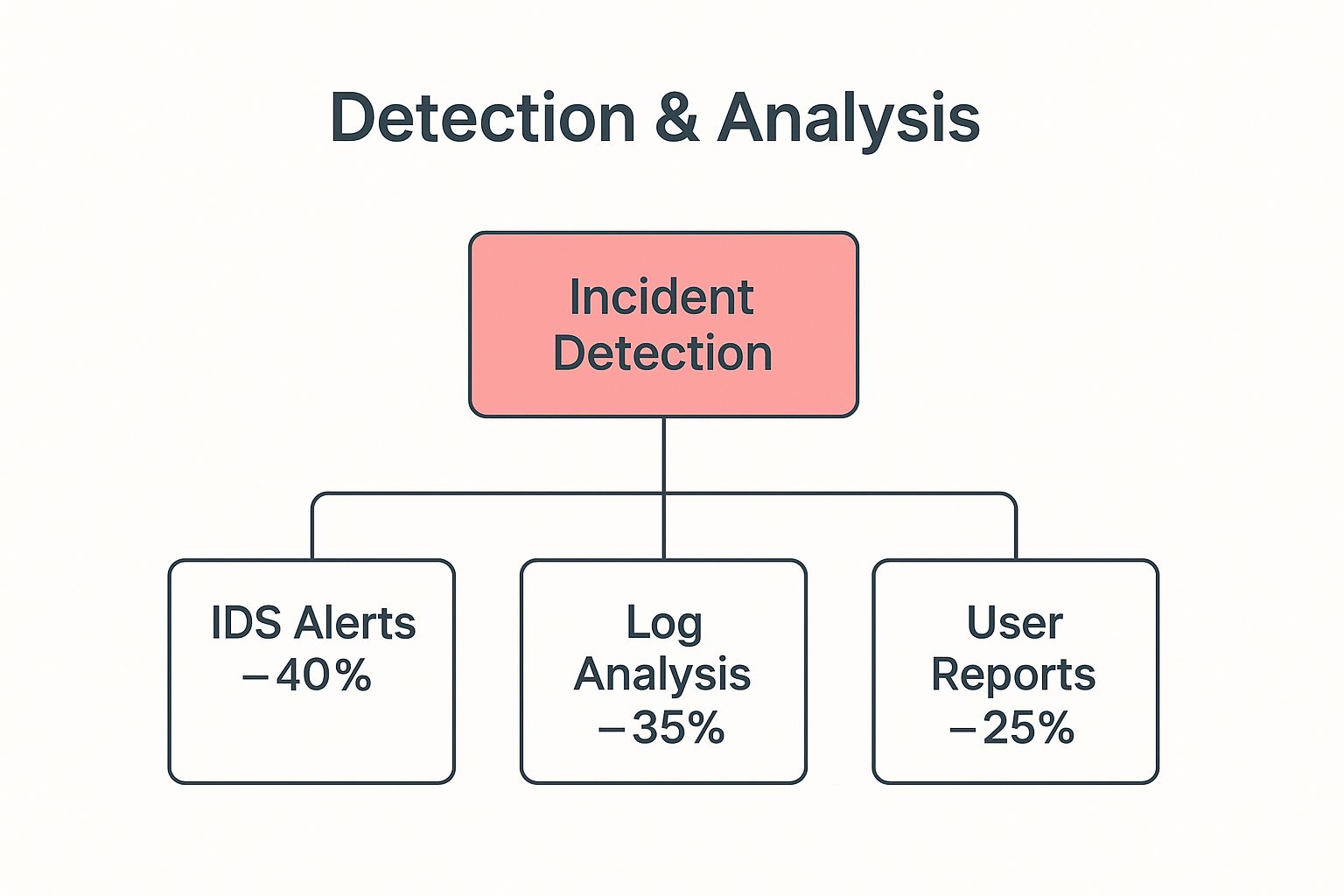
As you can see, while automated alerts are important, human-led activities like log analysis and even simple user reports are often how breaches are first discovered. This really drives home the need for an experienced team.
Knowing When to Call in the Experts
Let's be realistic: no company has an in-house expert for everything. Acknowledging the limits of your internal team and knowing when to bring in outside help is a mark of a truly mature response strategy. These specialists offer niche skills that can be the difference between a managed incident and a full-blown catastrophe.
For smaller professional services firms, trying to cover every aspect of IT security can be a real stretch. This is where exploring managed IT support and services can be a game-changer, giving you access to high-level expertise without the cost of a large internal department.
Think about engaging a digital forensics firm to dig deep into a sophisticated attack or bringing in a specialist PR agency to handle communications and protect your hard-won reputation. The key is to have these relationships in place before you need them.
A crisis is the worst possible time to be vetting suppliers. Get external forensics, legal, and communications experts on retainer now. When an incident happens, you can activate them with a single phone call instead of wasting precious hours trying to find someone to help.
To help you get started, here’s a breakdown of the key roles you'll want to define for your own team.
Key Roles and Responsibilities in a Data Breach Response Team
This table provides a solid blueprint for structuring your team. It maps out the essential roles, what they're responsible for during an incident, and the skills they need to succeed.
| Role | Primary Responsibilities | Essential Skills |
|---|---|---|
| Incident Lead | Oversees the entire response, coordinates team efforts, communicates with executive leadership. | Strong leadership, decisive decision-making, excellent communication, crisis management. |
| IT Security | Investigates the breach, contains the threat, preserves evidence, restores systems. | Deep technical knowledge, network analysis, malware forensics, system administration. |
| Legal Counsel | Ensures ICO/GDPR compliance, advises on legal risks, manages external legal engagement. | Expertise in UK data protection law, risk assessment, evidence handling procedures. |
| Communications Lead | Manages internal and external messaging, liaises with PR firms, drafts notifications. | Public relations, clear writing, stakeholder management, calmness under pressure. |
| HR Representative | Handles employee-related issues, manages internal communications about the breach. | Employee relations, internal communication strategies, policy enforcement. |
Having these roles clearly defined and assigned to capable individuals is the foundation of a response that is controlled, compliant, and effective.
Containing the Breach and Assessing the Impact
Once your response team is activated, the game immediately changes to damage control. This is the moment when things get real—a high-pressure phase where two critical tasks have to happen at once: containing the breach to stop the bleeding and assessing the impact to figure out what’s been hit. The calls you make here will shape everything that follows, from the ultimate severity of the incident to how well you recover.

Let's be clear: this isn't about finding a perfect, silver-bullet solution on the spot. It's about taking quick, decisive action to isolate the affected systems and stop a localised fire from turning into a company-wide inferno. All the while, you’ve got to be incredibly careful to preserve the digital evidence needed for the investigation that’s sure to come.
Practical Strategies for Breach Containment
Think of containment as pulling up the drawbridge. Your immediate goal is to cut off the attacker's access and stop them from moving laterally across your network. The right move here depends entirely on the type of attack and your own unique setup.
Let’s take a real-world scenario. Imagine a UK consultancy gets hit with ransomware. The attackers found a way in through a compromised supplier account and are now busy encrypting files on a central server holding client project data. The IT security team has to act, and fast. Their options might include:
- Network Segmentation: The best first move is almost always to isolate the infected server. That could mean literally pulling the network cable, but more realistically, it involves using network controls to block all its communication. This stops the ransomware dead in its tracks.
- Revoking Credentials: That compromised supplier account needs to be shut down immediately. This means changing passwords, revoking any access tokens or API keys, and slamming the door on the attacker’s entry point.
- Blocking Malicious IP Addresses: If the initial analysis spots traffic from specific IP addresses linked to the attacker, get those blocked at the firewall. This can sever their command-and-control connection.
Choosing the right option requires a calm, clear head. Taking a critical server offline will almost certainly impact business operations, but leaving it connected could mean your entire dataset gets encrypted. This is where a well-rehearsed data breach response plan is worth its weight in gold, as it should already outline the acceptable risks and who has the authority to make these tough calls.
Assessing the Scope and Severity of the Damage
While your technical team is fighting the fire, a parallel investigation must kick off to figure out the full extent of the breach. This is far more than just a tech exercise; it's a crucial step for meeting your legal obligations under UK GDPR. You absolutely must know what data was involved to understand the potential harm to individuals.
Your assessment needs to answer a few key questions:
- What systems were affected? Get a definitive list of every server, laptop, and application that was compromised.
- What data was accessed or exfiltrated? You need to know the categories and volume of data. Was it client PII, company financial records, or sensitive intellectual property?
- Was the data altered or deleted? Assess the data’s integrity. Ransomware encrypts files, but other attacks might be more subtle, silently altering records.
During this phase, preserving digital evidence is non-negotiable. Forensic images—exact copies—of affected systems must be taken before anyone starts trying to fix things. These snapshots are vital for understanding the attacker’s methods and will be essential if you need to involve law enforcement. The sheer complexity here really underlines the importance of knowing what to do after a cyber attack to avoid accidentally destroying the evidence you need.
The initial damage assessment is often just a best guess based on limited information. Treat it as a living document and update it constantly as your forensic investigation brings new facts to light. This agile approach ensures your response stays grounded in reality.
The financial and operational fallout from cyberattacks in the UK shows just how critical these response plans are. For instance, ransomware is a persistent threat, now featuring in 44% of UK incidents. High-profile cases, like the £32.7 million financial hit on NHS partner Synnovis and the £6–7 million recovery cost for the British Library, are stark reminders of why a well-practised playbook is essential.
These plans must have clear isolation steps, rapid restoration processes, and a solid crisis communications strategy to limit both the financial and reputational damage. And with third parties now involved in around 30% of breaches, managing supplier risk has to be a core part of any modern security framework. You can dig into the latest government report on the findings from the Cyber Security Breaches Survey for more detail.
By systematically containing the threat while assessing its impact, you build the foundation for a controlled, effective recovery—turning chaos into a structured response.
Managing Communications and UK Legal Duties
How you handle communications during a data breach can make or break your reputation. It’s a moment of truth. When the pressure mounts, a calm, strategic, and human approach is your best defence for maintaining trust with everyone from your staff to your clients and, of course, the regulators. You're walking a tightrope: be transparent enough to be credible, but not so open that you create a panic, all while staying on the right side of the UK’s tough legal framework.
At the core of your legal obligations is the UK General Data Protection Regulation (UK GDPR), which gives you a notoriously short window to act. You have just 72 hours from the moment you realise a breach has occurred to report it to the Information Commissioner's Office (ICO). But there's a crucial caveat – this only applies if the breach poses a risk to people's rights and freedoms. This isn't a guideline; it's a hard deadline with hefty fines for missing it.
Navigating the ICO Reporting Deadline
That 72-hour clock starts ticking the second you have a reasonable degree of certainty that a security incident has compromised personal data. Your initial assessment, therefore, is everything. There’s simply no time to waste.
Deciding whether you even need to report isn't always black and white. You have to ask yourself: is this breach likely to result in a risk to individuals? Think about the real-world impact. This could be anything from:
- The risk of identity theft or outright fraud.
- Direct financial loss.
- Serious damage to someone's reputation.
- A breach of confidential information, like medical records or legal files.
Let’s put this into practice. Imagine a marketing agency’s server is hit, but the data accessed was already anonymised and heavily encrypted. The risk is probably low, so an ICO report might not be necessary. Contrast that with a law firm that suffers a ransomware attack, exposing sensitive client case files full of personal and financial details. Here, the risk is incredibly high, and reporting to the ICO is non-negotiable. Getting this right is critical, and our GDPR compliance checklist is a great resource for making sure your internal processes are up to scratch.
Crafting Your Communication Strategy
A solid communication plan has to speak to different groups of people, each with their own distinct concerns. One of your first moves should be getting a holding statement out. Knowing how to write a holding statement for a PR crisis is an invaluable skill; it gives you breathing room while showing you’re on top of the situation.
From there, you need to tailor your message.
- Employees: Tell your team first. Give them clear, simple instructions on what they can and can’t say. Funnel all questions through a single point of contact to keep your messaging consistent.
- Affected Individuals: If the breach poses a high risk to them, you are legally required to inform them directly and without "undue delay." Be straight with them. Explain what happened, what data was involved, what the potential fallout could be, and what you’re doing to help.
- Regulators (ICO): The ICO report needs to be factual, not emotional. Stick to the details: the nature of the breach, the types of data and rough numbers of people affected, and the contact details for your Data Protection Officer or main point of contact.
- The Public/Media: For a major incident, a public statement is unavoidable. Your tone here should be one of transparency and empathy. Acknowledge the failure, explain what you're doing to fix it, and show you care.
I’ve seen companies make the classic mistake of hiding behind corporate jargon and legalese. In a crisis, people don’t want a press release; they want clear, honest information. Acknowledge what happened, express genuine regret, and focus on the practical steps you’re taking to protect them.
Cyber attacks are a fact of life for UK businesses. A recent government survey found that a staggering 43% of UK businesses had experienced a breach or attack. Phishing is still the number one culprit, involved in 85% of these incidents. This just goes to show why a robust data breach response plan absolutely must have clear communication protocols ready to go for this very common scenario. With attackers now using generative AI to make their phishing attempts more convincing, a well-rehearsed response has never been more vital.
Ultimately, getting your communications and legal duties right comes down to one thing: preparation. Having pre-approved message templates and a clear chain of command in place means you can act swiftly, stay compliant, and focus on protecting the people who matter most – your clients and your employees.
Learning From the Incident to Strengthen Your Defences
Once the immediate chaos of a data breach subsides, the real work begins. The final, and I’d argue most critical, phase of any response is to learn from what just happened. This post-incident review is what turns a crisis from a purely negative event into a powerful opportunity to build genuine, long-term cyber resilience.

Let’s be clear: this isn't about pointing fingers. A successful review is a "blameless post-mortem." The focus is squarely on uncovering weaknesses in your processes, technology, and staff awareness. It’s a chance to ask tough questions and get honest answers that will directly improve your security posture.
Conducting a Structured Post-Incident Review
After the dust settles, it’s vital to get your entire incident response team in a room for a structured debrief. The goal is to build a detailed timeline of the incident, from the first flicker of detection to the final resolution, and analyse every decision made along the way. Without this formal process, valuable lessons get lost in the shuffle as everyone rushes back to their day-to-day tasks.
To keep the discussion on track, I recommend focusing on a few key areas:
- Detection and Escalation: How did we first find out about this? Was it an automated alert, a staff member raising a flag, or—worst case—a call from a third party? How quickly did we sound the alarm and get the response team moving?
- Response Effectiveness: Did the team have everything they needed to act decisively? Were our containment procedures actually effective in stopping the bleed?
- Communication: How well did our internal and external communications hold up under pressure? Were the messages clear, timely, and consistent across the board?
- Plan Adherence: Did we actually follow our data breach response plan? If we went off-script, why was that necessary?
An honest appraisal here will quickly show you what worked and, more importantly, what broke.
The single biggest mistake a business can make after a breach is failing to learn from it. Each incident provides a unique, real-world stress test of your defences. Ignoring the lessons it offers is an open invitation for a repeat performance.
Analysing Timelines and Identifying Gaps
Timelines are your best friend when it comes to understanding how effective your response really was. Any delay, at any stage, can massively amplify the damage.
Consider this: in the UK, it takes organisations an average of 241 days to detect and fully contain a data breach. That’s a shocking figure. The average time just to detect the intrusion is 181 days, giving attackers a huge window to roam around a network completely undetected.
These numbers reveal a common blind spot—a lack of the continuous monitoring needed for rapid detection and response. By reviewing your own incident timeline, you can pinpoint exactly where your delays happened, whether it was in detection, analysis, or containment.
Creating an Actionable Improvement Plan
The result of your review can't just be a report that gathers dust. It needs to be a concrete, actionable improvement plan with clear owners and non-negotiable deadlines. This isn't a theoretical exercise; it’s about making tangible changes to stop this from happening again.
Your improvement plan should tackle three core pillars:
- Updating the Response Plan: Use what you’ve learned to refine your data breach response plan. This could mean clarifying roles that were ambiguous, sharpening up communication templates, or streamlining escalation procedures to be faster and more efficient.
- Hardening Technical Defences: You have to address the technical root cause. This might mean patching the specific vulnerability that was hit, finally rolling out multi-factor authentication across the board, or improving your network segmentation. A key part of this is looking ahead, and a comprehensive threat and vulnerability management guide can help you proactively identify and fix other potential weaknesses before they get exploited.
- Refining Employee Training: If human error was a factor, like someone falling for a phishing email, don't shy away from it. Use the incident as a real-world case study in your next security awareness session. Training that uses recent, relevant examples is far more powerful than any generic guidance.
By systematically dissecting the incident and turning your findings into a practical strategy, you ensure the painful experience of a breach becomes a valuable investment in your organisation’s future security.
Got Questions About Your UK Data Breach Response Plan?
When you're in the thick of managing a potential data breach, theory goes out the window. Practical questions bubble up fast. Let's tackle some of the most common queries we hear from UK professional services firms trying to get their incident response plans right.
How Often Should We Actually Test Our Plan?
A plan gathering dust in a folder is useless. To be confident it will hold up under real-world pressure, you need to test it at least annually. A simple tabletop exercise is a great way to do this – just get the response team in a room and walk through a realistic scenario. For a professional services firm, this could be simulating a ransomware attack on your client database just before a major deadline.
However, if your business operates in a high-risk sector like law or finance, or if you've recently gone through big changes like a merger, you should really be testing quarterly. The goal of regular testing isn't just to tick a box; it's to build muscle memory so your team's response becomes second nature when the worst happens.
What’s the Single Biggest Mistake We Could Make?
Without a doubt, the most damaging mistake UK companies make is hesitating. This delay can kill your response in two critical ways: you either fail to move fast enough to contain the breach, or you put off reporting it to the Information Commissioner's Office (ICO) past the crucial 72-hour window.
In a data breach situation, procrastination is your worst enemy. Every moment you spend second-guessing allows attackers to dig deeper, and it can turn a manageable incident into a regulatory nightmare that shatters client trust. Decisive action is everything.
Imagine a consultancy spending four days debating whether an incident is "serious" enough to report. By the time they make a decision, they've already violated UK GDPR. That initial hesitation has just guaranteed them a compliance headache on top of the breach itself.
Do We Really Need to Tell the ICO About Every Little Hiccup?
No, you don't. The line in the sand, according to UK GDPR, is whether the breach is likely to result in a risk to the rights and freedoms of individuals. This isn't a gut feeling; it demands a proper, documented risk assessment for every single incident.
For instance, say an employee’s laptop is stolen. If the hard drive is fully encrypted to modern standards, the actual risk to personal data is probably minimal, so you likely wouldn't need to report it. But if an unencrypted client database gets into the wrong hands, the potential for identity theft and fraud is enormous. That's a definite report.
When assessing an incident, ask yourself:
- What kind of data was it? Was it sensitive information, like legal files or financial details?
- How many people were affected? Was it a handful of records or thousands?
- What’s the potential fallout? Could this lead to real harm for the people involved, such as financial loss or serious reputational damage?
The key is to document everything. Even if you decide not to report a breach, you must have a clear record showing why you made that call, just in case the ICO ever comes knocking.
A solid data breach response plan is a non-negotiable part of business resilience today. For over 30 years, SES Computers has delivered expert managed IT support and cybersecurity services to businesses across Dorset, Hampshire, and the surrounding areas, helping them prepare for and navigate security incidents. Find out how we can strengthen your defences at https://www.sescomputers.com.