How to Monitor Network Traffic Like a Pro
Monitoring network traffic is about much more than just watching data packets fly by. It's about using the right tools to capture, analyse, and report on everything happening across your company’s network. Done right, this process lets you pinpoint performance bottlenecks, spot security threats before they cause damage, and make sure your resources are being used wisely.
For any professional services firm, this isn't just a technical task—it's a fundamental part of your business strategy.
Why Proactive Network Monitoring Is Essential

Simply reacting to network problems when they pop up is a recipe for disaster. In today’s competitive world, even a brief slowdown can halt productivity, frustrate clients, and tarnish your hard-won reputation.
Proactive monitoring completely flips the script. Instead of constantly firefighting, you get ahead of problems, addressing them before they become full-blown crises. The conversation shifts from, "Why is the system down again?" to "How can we make our network faster and more secure?"
Think of a financial advisory firm during volatile market conditions. If the network stumbles, advisers could lose access to critical trading platforms. This could delay client trades, leading to very real financial losses and regulatory scrutiny. That is the tangible risk you run with an unmonitored network.
Uncovering Hidden Risks and Inefficiencies
Without clear visibility, your network can easily become a hotbed for hidden threats and wasted money. Employees might be using unauthorised applications that secretly hog bandwidth or, even worse, introduce serious security holes.
Here's a practical example: a marketing agency’s network ground to a halt every afternoon, crippling their video calls and large file transfers. The reactive approach would be to blame the internet provider. The proactive one, using traffic analysis, revealed the real culprit in minutes—an unsanctioned cloud backup service was synchronising terabytes of data right in the middle of the business day.
Understanding exactly what is travelling across your network transforms raw data into powerful, actionable intelligence. This insight is what allows you to protect your operations, strengthen your security, and drive real efficiency.
Safeguarding Your Business in a Complex Environment
This need for visibility is especially critical given the UK's increasingly complex telecommunications landscape. We're now dealing with a mixture of traditional fixed lines, full fibre, and growing fixed wireless access (FWA) networks.
As of early 2025, Ofcom's reports highlight this technological patchwork, making it clear that a one-size-fits-all approach won't work. Your monitoring strategy needs to be sophisticated enough to handle different network types at the same time. This complexity demands real-time, detailed analysis to guarantee both quality of service and security. You can get a clearer picture of the national infrastructure from the Connected Nations Update from Ofcom.
Ultimately, learning how to monitor network traffic effectively gives any professional services business a serious advantage.
- Enhanced Security: Spotting unusual activity, like large, unexpected outbound data transfers, can be the first sign of a data breach or malware.
- Improved Performance: You can quickly identify bandwidth-hogging applications or users and reallocate resources to ensure your most critical business systems always run smoothly.
- Informed Capacity Planning: Analysing traffic trends over time provides the hard data you need to make smart decisions about future upgrades, so you can scale efficiently without overspending.
Choosing the Right Network Monitoring Tools
Selecting the right solution to monitor network traffic is a make-or-break decision for any professional services firm. With so many options out there, it’s easy to feel overwhelmed. The secret isn't finding the most feature-packed tool, but rather the one that directly solves your biggest business challenges—whether that’s protecting sensitive client data or ensuring your critical applications run smoothly.
Your choice of tool fundamentally shapes your ability to truly understand what's happening on your network. Different tools provide vastly different perspectives, from a high-level overview to a microscopic inspection of data packets. Understanding these distinctions is the first real step towards making a smart investment.
A Look at the Different Tool Categories
To simplify things, network monitoring tools generally fall into a few key categories. Each has its own strengths, and the best one for you depends entirely on what you're trying to accomplish. For example, a financial services firm will likely prioritise deep security analysis, while a creative agency might be more concerned with managing bandwidth for those massive file transfers.
To help you decide, I’ve broken down the main approaches into this comparison table. It gives a clear view of where each tool type shines.
Comparison of Network Monitoring Tool Types
| Tool Type | Best For | Key Advantage | Practical Use Case for a Professional Service |
|---|---|---|---|
| Packet Sniffers | Deep-dive troubleshooting and security forensics. | Granular detail, capturing individual data packets. | An accountancy firm diagnosing why a specific user intermittently loses connection to the HMRC portal. |
| Flow-Based Analysers | High-level traffic pattern analysis. | Efficiency; provides insights without massive storage needs. | A law firm identifying which department is using the most bandwidth to plan for a network upgrade. |
| NPM Platforms | Holistic view of network and application health. | Comprehensive dashboards and a unified view of performance. | A consultancy proactively managing user experience for its cloud-based project management software. |
Ultimately, picking the right tool is about getting the specific insights your organisation needs to run securely and efficiently. A mismatch here often leads to wasted money and a flood of data that doesn't actually answer your most important questions.
Making the Right Decision for Your Business
Beyond the tool type, think about scalability, ease of use, and integration. If you're a growing business, you need a solution that can expand with you, not one you'll have to replace in a year. For those with a smaller IT team, an intuitive interface and smart, automated alerts are lifesavers, drastically cutting down the time spent manually staring at dashboards.
This infographic gives a great visual breakdown of typical network traffic, which really highlights why understanding these patterns is so crucial for managing your resources.
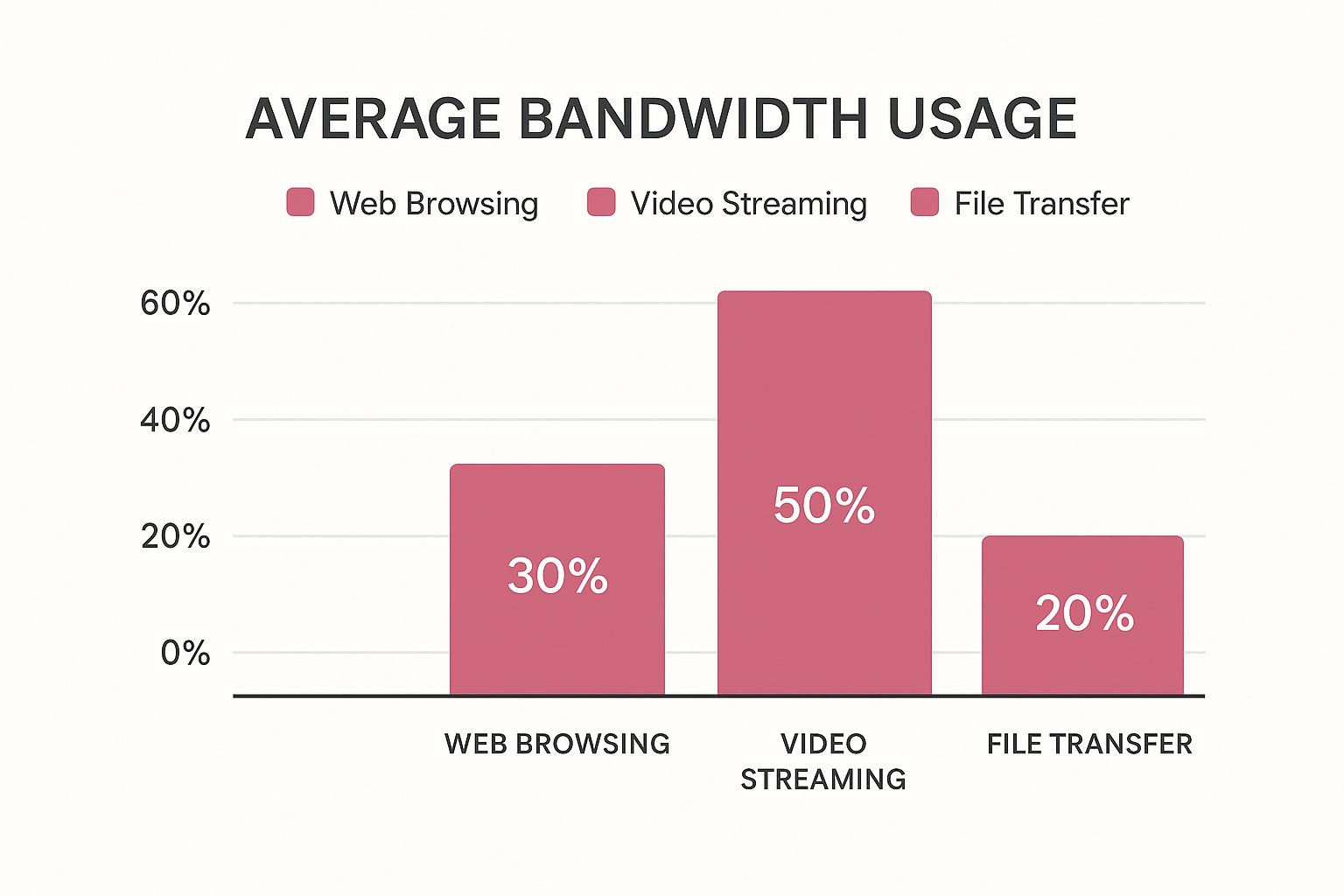
As the chart shows, video streaming is often the biggest bandwidth hog—a critical piece of information when you're choosing a tool to manage network performance.
And if you’re ready to start shortlisting specific products, this review of the 12 Best Network Performance Monitoring Tools for 2025 is an excellent resource to help you narrow down the options.
Configuring Your System for Effective Analysis

Any experienced engineer will tell you that the most powerful monitoring tool is only as good as its configuration. Simply installing software and leaving it on the default settings won't get you very far. The real value comes from setting up a monitoring environment that’s tuned specifically to your business goals and delivers genuinely useful data.
The absolute first thing you need to do is establish a performance baseline. Think of this as a detailed portrait of your network operating under normal, everyday conditions. By measuring key metrics like traffic volumes, application latency, and device performance over a typical week or even a month, you create a clear picture of what ‘healthy’ looks like for your organisation.
This baseline is your benchmark. It's the standard against which all future activity is measured. Without it, you’re flying blind. A sudden surge in bandwidth could be a critical issue, or it could just be the weekly server backup kicking in. A solid baseline tells you the difference.
Setting Up Your Data Collection Points
To build that baseline, you need to collect the right data. This means telling your network hardware where to send traffic information for analysis. In our experience, there are two go-to methods for this: using a Switched Port Analyser (SPAN) port or a dedicated network TAP (Test Access Point).
- SPAN Ports: These are built into most business-grade switches and allow you to mirror traffic from one or more ports to a single port connected to your monitoring tool. It's a very cost-effective way to get started.
- Network TAPs: These are dedicated hardware devices that you place in-line on a network link. They create a perfect copy of all traffic without adding any load to the switch itself, making them the more reliable choice for high-traffic or mission-critical links.
Your decision here will likely come down to your budget and how critical the links you're monitoring are. You can also configure flow data exports (like NetFlow or sFlow) from your routers to get a high-level overview of traffic patterns without the overhead of capturing every single packet. Properly handling this influx of information is crucial, which is where understanding solid Extract, Transform, Load (ETL) processes becomes essential for preparing data accurately.
To get the most out of these hardware configurations, it helps to have a well-optimised foundation. We've shared some guidance on fine-tuning your routers and switching infrastructure that you might find useful.
Creating Alerts That Matter
With data flowing into your system, the next challenge is to create alerts that actually mean something. The aim is to avoid the dreaded ‘alert fatigue’—a situation where your IT team is bombarded with so many meaningless notifications that they start to ignore the important ones.
A practical example is setting up a highly specific alert for unusual outbound traffic from your client database server. If a workstation suddenly starts uploading gigabytes of data to an unknown IP address in the middle of the night, that’s a massive red flag for a potential security breach or data exfiltration.
This is far more valuable than a generic "high bandwidth" alert. The same logic applies to performance. If latency to a critical cloud application suddenly spikes well above its normal baseline, you want an immediate, targeted alert that helps you start troubleshooting right away. Context is everything.
Turning Traffic Data into Actionable Insights
So, you've got your monitoring tools set up and data is pouring in. That’s the easy part. The real work—and where you’ll find the value—is in making sense of it all. This is the moment you stop just collecting numbers and start building a clear picture of your network's health, security, and overall efficiency.
Learning to read this story is what separates a reactive admin from a strategic one. It's about taking raw information and shaping it into smart decisions. For a deeper dive into this process, this practical guide to turning data into actionable insights is a fantastic resource.
Identifying Top Talkers and Bandwidth Hogs
Your first port of call should almost always be identifying your network's ‘top talkers’. These are the devices, users, or applications gobbling up the most bandwidth. Most good monitoring tools will have a report that lays this out clearly, showing you exactly where your resources are being spent.
This isn't about blaming users. It's about understanding behaviour. For instance, you might see that the marketing team’s video work is responsible for 40% of your daily bandwidth use. Armed with that knowledge, you can have a constructive chat about maybe scheduling those massive file transfers for after hours, which frees up critical bandwidth for everyone else during the day.
A Real-World Example: We once assisted a law firm in Dorset that was plagued by crippling network slowdowns every single Tuesday morning. A quick glance at their 'top talkers' report pointed the finger at one server. Digging a little deeper, we found a misconfigured backup job that was failing and retrying repeatedly, chewing through bandwidth long after everyone had arrived for work. A simple tweak to the schedule fixed the issue permanently.
Spotting Unusual Patterns for Security
Beyond just performance, traffic analysis is one of your strongest security allies. Once you have a solid baseline of what ‘normal’ network activity looks like, anything that deviates from it should set off alarm bells. These anomalies are often the first sign of a security breach.
Your monitoring tools are your eyes on the network, helping you spot these tell-tale signs:
- Sudden spikes in outbound traffic: If a workstation that typically sends out a few megabytes a day suddenly starts pushing gigabytes to a strange destination, you could be looking at data theft or a malware infection.
- Unusual port activity: Seeing traffic on non-standard ports can be a red flag. It often signals an attempt to tunnel past your firewall or establish a hidden communication channel.
- Connections to known malicious IPs: Modern tools are brilliant at this. They can check traffic destinations against live threat intelligence feeds and alert you the moment a device on your network tries to talk to a known command-and-control server.
Diagnosing Application Performance Problems
When a business-critical application starts to crawl, the finger-pointing begins. Is it the application itself? The server it lives on? Or is the network at fault? Traffic analysis cuts through the noise and gives you the hard evidence to find the real culprit.
By looking at metrics like latency and packet loss for specific traffic flows, you can quickly see if the network is the bottleneck. High latency between a user and a cloud service, for instance, points squarely at a connectivity problem. This kind of data lets you focus your troubleshooting efforts where they'll actually make a difference, getting your professional services team back up and running with minimal disruption.
Weaving Monitoring into Your Broader Business Strategy
Truly effective network monitoring is about so much more than just keeping the lights on in the server room. The data you gather isn't merely for troubleshooting glitches; it's a goldmine of business intelligence that can genuinely shape your company's future. When you start weaving traffic analysis into your wider strategy, you give your entire organisation the power to make smarter, data-driven decisions.
This strategic mindset completely reframes how network management is viewed. It stops being a simple cost centre and starts being recognised as a function that delivers real, tangible business value. Learning how to monitor network traffic with a strategic eye gives IT leaders the hard evidence they need to justify investments and prove their direct impact on the bottom line.
Justifying Infrastructure Investments
When it’s budget season and time to ask for a network upgrade, simply saying "things are a bit slow" isn't going to convince the board. You need to build a compelling business case, and that means bringing hard data to the table. This is where network monitoring becomes your best friend.
For instance, imagine you've noticed that latency to your cloud-based CRM is creeping up, directly hampering your sales team's ability to log calls and update client files. By presenting this data, you can draw a straight line between network performance and team productivity.
- The old way: "The sales team is complaining the CRM is slow."
- The data-driven way: "Our monitoring tools show a 35% increase in latency to our CRM during peak business hours. This directly correlates with a 15% drop in logged sales activities. A £5,000 investment in a dedicated leased line will eliminate this bottleneck, boosting productivity and helping us hit our revenue targets."
Demonstrating Regulatory Compliance
For any professional services firm today, proving compliance with data protection laws like GDPR is non-negotiable. It is a fundamental legal requirement. Your network traffic monitoring is a critical piece of the puzzle for proving you're safeguarding sensitive client information.
By keeping detailed logs of all data flows, you create a complete, auditable trail. This lets you show regulators precisely where data is going, who is accessing it, and, crucially, that it isn't being moved to unauthorised locations. This kind of proactive documentation is invaluable when a compliance audit comes knocking.
Informing Capacity Planning and Growth
This strategic view is also vital for planning your future. Think about the challenge of managing national infrastructure, a concept well understood in UK transport. Provisional government estimates show vehicle miles on Great Britain's roads reached a staggering 335.9 billion between 2024 and 2025. This scale requires incredibly intelligent systems to monitor the huge flow of data from sensors and cameras just to prevent gridlock. You can read more about the UK's approach to traffic management.
Your business network needs the same forward-thinking management. By analysing traffic trends over months or even years, you can get ahead of future demand. This allows you to accurately forecast when you’ll need more bandwidth or faster connections, letting you scale your infrastructure smoothly and cost-effectively. You're no longer just reacting; you're ensuring your network is always ready to support your business ambitions.
Your Network Monitoring Questions, Answered
Even with the best plan, you're bound to have questions when you first dive into monitoring your network traffic. Let's tackle some of the most common ones we hear from professional services firms, providing clear answers to help you get started with confidence.
What’s the Difference Between Active and Passive Monitoring?
This is a great question, and it gets to the heart of monitoring techniques.
Think of passive monitoring as being a silent observer on the sidelines. Your tools, like SPAN ports or network TAPs, make a copy of the live traffic and analyse it without ever getting in the way of the actual data flow. It’s fantastic for getting a true baseline of your network's behaviour, seeing who’s using all the bandwidth, and spotting security issues that might otherwise fly under the radar.
Active monitoring, on the other hand, is more hands-on. It actually sends out its own test packets to check the network's health and performance. It’s like sending a scout ahead to make sure the path is clear. This method is perfect for confirming that key services are reachable, measuring latency to a specific application, and running health checks on your critical servers and routers.
In reality, a strong monitoring strategy will almost always use a blend of both.
Can the Monitoring Tools Themselves Create a Security Risk?
This is a completely valid and important concern. Anytime you give a tool that kind of deep access to your network traffic, you need to be careful. If it's not managed correctly, it can introduce risk. The good news is that any reputable monitoring solution is built with security as a top priority.
The secret is in the setup. You need to implement the tools securely. This means locking down access to the monitoring platform itself, enforcing strong authentication for anyone who uses it, and making sure the data it gathers is encrypted, both when it's moving across the network and when it's stored.
When you configure it properly, the security boost you get from finding threats early far outweighs the manageable risks.
The biggest risk, in our experience, is flying blind. Too many businesses only find out about a vulnerability after they've been breached. Proactive monitoring flips that script, helping you find and fix those weak points before an attacker does. To get a better sense of what's at stake, it's worth understanding the common cybersecurity threats that managed services can shield your business from.
How Can I Start Monitoring if My Budget Is Tight?
You absolutely don't need a massive budget to get started. Plenty of organisations begin by using incredibly powerful open-source tools. For instance, Wireshark is the gold standard for deep packet analysis, and solutions like Zabbix can give you amazing performance insights—all without any software licensing costs.
Here’s a practical path for getting started on a shoestring:
- Look at what you already own. Start by turning on the flow data features (like NetFlow or sFlow) that are probably built right into your existing routers and switches. This alone gives you a high-level view without any new investment.
- Install open-source software. Set up a dedicated machine and install an open-source tool to collect and make sense of all that flow data.
- Pick one critical spot. Don't try to boil the ocean. Zero in on your most important asset, whether that's your main internet connection or the server running your most critical business application.
This approach lets you prove the value of monitoring very quickly and on a small scale. Once you can show tangible results, it becomes much easier to make the case for investing in more advanced commercial tools down the road. Start small, show a win, and build from there.
Ready to gain complete visibility and control over your network? The expert team at SES Computers provides proactive monitoring and managed IT services that protect your business, boost performance, and give you peace of mind. Contact us today to find out how we can help.