IT Security Awareness Training for UK Businesses
IT security awareness training is all about turning your employees from your biggest potential security weakness into your strongest defensive asset. It’s a continuous process of teaching your team how to spot, report, and fend off cyber threats, effectively creating a human firewall across your entire organisation.
Your First Line of Defence Against Cyber Threats

Think of your business as a castle. You've invested in high walls (firewalls), reinforced gates (access controls), and guards on the towers (monitoring software). But what happens if one of your own team is tricked into lowering the drawbridge for a friendly-looking stranger? Suddenly, all those expensive defences are rendered useless.
This is precisely where IT security awareness training comes in. The goal isn't to make everyone a cybersecurity guru. It’s about giving your team the practical skills to recognise and question things that don't feel right, much like a gatekeeper is trained to verify someone’s identity before letting them in.
For professional services firms across the UK—from legal practices in Hampshire to accountancy firms in Dorset—this is no longer a 'nice-to-have'. It’s an essential part of keeping the business running and protecting client trust. The hard truth is that human error is a factor in the vast majority of security breaches. One wrong click on a malicious link can have devastating consequences.
The Power of a Digital Fire Drill
It helps to think of security awareness training as a regular digital fire drill. You wouldn't just give a single talk on fire safety and assume everyone will remember it in a panic. You run drills. That repetition ensures everyone knows the escape routes and how to act calmly when the alarm bells ring. Cybersecurity is exactly the same.
Effective IT security awareness training is about building muscle memory. It ingrains secure behaviours into daily routines so that spotting a phishing email or questioning an unusual request becomes second nature, not an afterthought.
This proactive mindset shifts your staff from being the most common target for cyber attacks to being your most valuable detection layer. Automated tools are crucial, but clever attackers can find ways around them. An alert, well-trained employee, on the other hand, provides a dynamic defence that can spot new and unexpected threats.
This investment pays dividends that go far beyond just ticking a compliance box. By fostering a strong security culture, you're actively protecting:
- Your Finances: Preventing costly incidents like ransomware attacks or fraudulent payments.
- Your Reputation: Showing clients you take their data protection seriously, which builds invaluable trust.
- Your Operations: Avoiding the significant downtime and chaos that a security breach can cause.
Take this practical example: an accountant at a busy law firm receives an urgent email, supposedly from a senior partner, demanding an immediate payment to a new supplier to finalise a property deal. Training gives them the confidence to pause. It empowers them to verify the request through a separate, trusted channel—like a quick phone call—instead of getting swept up in the fake urgency. That simple, learned behaviour can stop a six-figure loss in its tracks.
Ultimately, effective IT security awareness training creates a shared sense of responsibility. It builds a culture where security isn't just "the IT department's problem" but a collective commitment. This is, without a doubt, the most powerful and cost-effective security investment any UK professional services firm can make.
The Urgent Cybersecurity Landscape in the UK

For UK businesses, the reality of cyber threats is stark and immediate. This isn't a far-off problem for giant corporations; it's a daily risk for organisations of every size, from accountancy firms in Dorset to architects in Hampshire. The threat is relentless, and the tactics attackers use are becoming alarmingly convincing.
Cybercriminals are masters of human psychology. They don't just hack systems; they hack people. Their attacks are carefully designed to exploit our natural tendencies—our instinct to trust, our reaction to urgency, and our capacity to make mistakes when under pressure.
This human element is where the real battle is fought. Without the right preparation, your team members, no matter how loyal or diligent, can unknowingly open the door to a devastating breach. It is for this very reason that a lack of effective IT security awareness training is one of the most critical vulnerabilities any UK business can have.
The Widening Gap Between Threat and Preparedness
Right now, a dangerous gap exists between the rising tide of cyber-attacks and how prepared employees are to handle them. This isn’t just a feeling; the official data paints a troubling picture. According to the UK Government’s Cyber Security Breaches Survey, a surprisingly small number of businesses are actually giving their staff the skills they need.
A significant challenge is the low uptake among employers: only 17% of businesses provide their staff with basic cybersecurity training, and just 19% test employees' responses to cyber incidents.
This training shortfall leaves countless UK organisations perilously exposed. Despite government encouragement, this lack of fundamental preparation means that far too many businesses are vulnerable to breaches that could lead to severe financial loss and reputational ruin.
Common Attack Methods That Target Untrained Staff
Attackers have a well-established playbook designed to bypass technical defences by going straight for your people. Knowing what these tactics look like is the first step in building a strong defence.
- Sophisticated Phishing Emails: Forget the poorly-written emails of the past. Today's phishing attacks can perfectly mimic legitimate messages from clients, suppliers, or even senior management. They create believable scenarios to trick an employee into clicking a dangerous link or handing over credentials.
- Ransomware Delivery: Often starting with a single click in a phishing email, a ransomware attack can encrypt your entire network and bring your business to a complete standstill. Attackers then demand a huge payment to restore your access, a scenario that has crippled many professional services firms.
- Business Email Compromise (BEC): In these scams, an attacker gets into a company email account to impersonate an employee. They might send fake invoices to your clients or trick your finance department into making unauthorised payments, siphoning money directly from your accounts.
While meeting compliance standards like GDPR is essential, it's really just the starting point. Genuine risk management means going further. Proactive IT security awareness training is the most direct and effective way to counter these human-focused threats. To learn more, explore our guide on the key cybersecurity threats that managed services can shield your business from. By preparing your staff, you're not just ticking a box—you're actively reducing risk and building a more resilient organisation.
Building Your Core Training Programme
So, you understand the 'why' of security awareness training. Now let's get into the 'what' and 'how'. Moving from theory to practice means building a training programme with a solid foundation of topics that genuinely matter to your team.
A great programme doesn't just throw a list of rules at people. It gives them the insight to spot real-world threats and the confidence to react properly. After all, the best training is directly relevant to an employee’s day-to-day work, not some abstract concept.
To get things rolling, you'll need a way to deliver the training effectively. Many businesses find that specialised Learning Management Systems (LMS) for training are a game-changer. They can track who has completed what, send out automated reminders, and present the material in a much more engaging way than a simple PowerPoint deck. Once you have your delivery method sorted, you can focus on the crucial part: the educational modules that will turn your staff into a strong human firewall.
Tackling Social Engineering Head-On
At its core, social engineering is the art of manipulation. Attackers play on human psychology—trust, urgency, or fear—rather than trying to find a technical loophole. It’s by far the most common way breaches happen, which makes it an absolutely critical part of your training. The goal here is to nurture a healthy sense of scepticism and make verification a natural reflex for your staff.
Your training must dive deep into phishing, the most common type of social engineering out there. Don't just define it; use realistic, everyday examples that your team can relate to.
Practical Example: Picture this. A junior solicitor at a busy law firm receives an email that appears to be from a senior partner. The subject line screams 'URGENT & CONFIDENTIAL', and the message demands an immediate wire transfer to a new supplier to close a property deal. The signature looks right, the tone is commanding. Without training, panic might set in. But with training, the solicitor spots the red flags—the sudden urgency, the highly unusual request, the new payment details. They know to pause, pick up the phone, and get verbal confirmation from the partner, stopping the attack in its tracks.
Mastering Password and Credential Security
It might sound basic, but weak or stolen passwords are still one of the main ways criminals gain entry to a network. People often don't realise how a single flimsy password can set off a catastrophic domino effect, leading to a massive breach. Your job is to guide them away from these risky habits and towards using strong, unique passwords for every single service.
Think of it this way: reusing a password is like using the same key for your house, your car, and your office safe. If a thief gets that one key, they have access to everything you own.
Practical Example: An employee at a consultancy firm uses their corporate password for a personal social media account. That social media site gets hacked, and the employee's login details are leaked online. Attackers immediately run automated scripts, trying those same leaked credentials on corporate login pages across the web. Before long, they're inside the consultancy’s network, with full access to sensitive client data. That one act of password reuse has just put client trust, major projects, and the firm’s entire reputation on the line.
The infographic below highlights just how much of a difference a focused training programme can make.
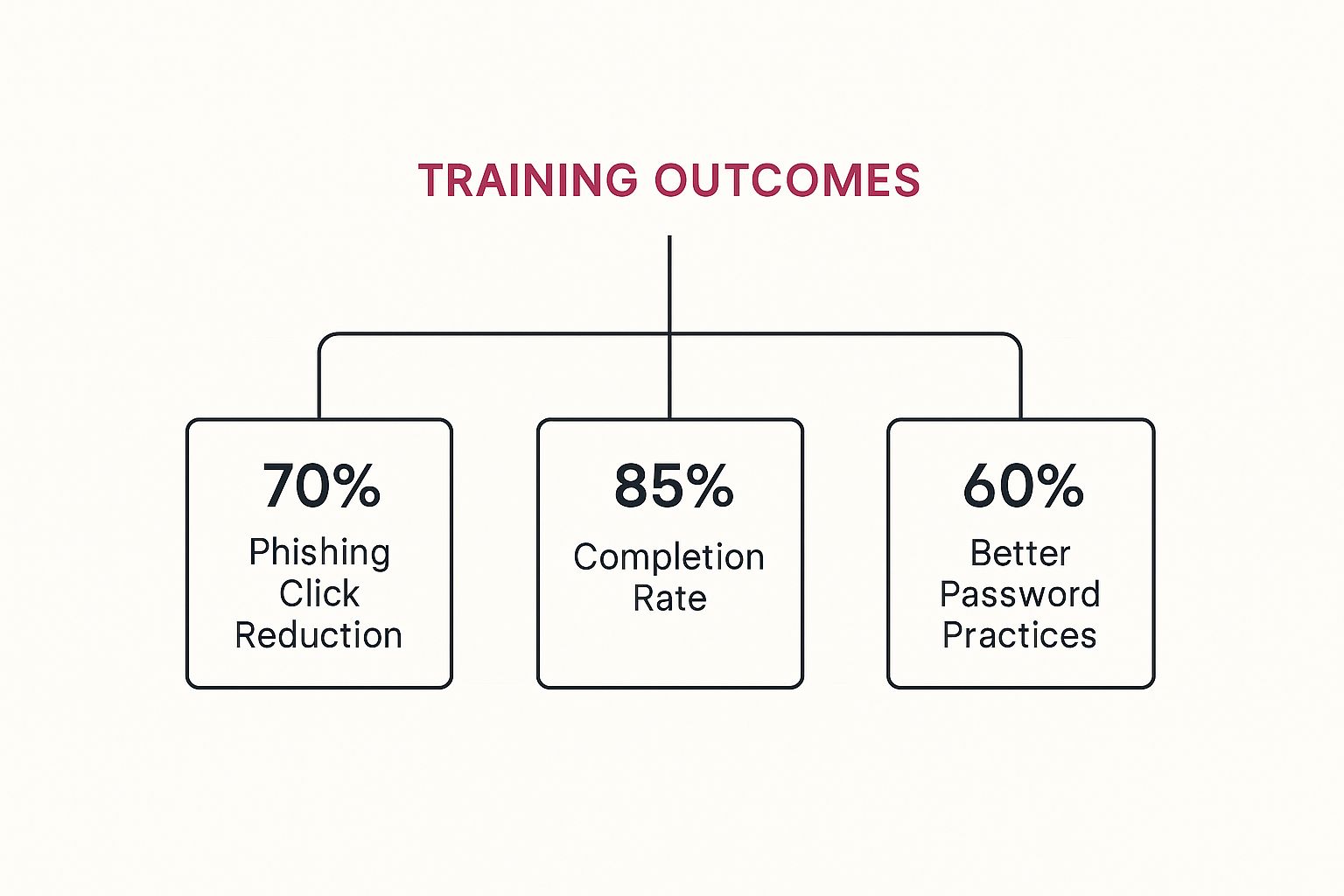
As the data shows, when you target specific behaviours with dedicated training, you get measurable improvements that strengthen your overall security.
The table below outlines some of the most critical topics to include in your programme. These modules form the backbone of a truly effective defence.
Essential Modules for a Comprehensive IT Security Awareness Programme
| Training Module | Key Learning Objective | Practical Business Example |
|---|---|---|
| Phishing & Social Engineering | To help staff identify and report suspicious emails, texts, and calls designed to trick them. | An employee receives an urgent SMS appearing to be from their bank, asking them to click a link to verify their account. They recognise it as a 'smishing' attempt, delete it, and report it to IT. |
| Password Hygiene | To enforce the use of strong, unique passwords and multi-factor authentication (MFA). | A staff member sets up MFA on their work accounts, meaning even if their password is stolen, a hacker can't log in without the second verification code from their phone. |
| Secure Data Handling | To ensure employees understand how to classify, store, and share sensitive information correctly. | A consultant uses the company’s approved encrypted file-sharing portal to send a client a confidential report, rather than attaching it to a standard email. |
| Physical Security | To build habits like locking screens, securing documents, and being aware of surroundings. | An employee working in a coffee shop always locks their laptop screen before stepping away to order, preventing anyone from snooping on sensitive client information. |
| Acceptable Use Policy (AUP) | To clarify what is and isn't permitted on company devices and networks. | An employee understands not to install unapproved software on their work laptop, which could introduce malware or create security vulnerabilities. |
| Incident Reporting | To empower employees to report potential security issues immediately without fear of blame. | After accidentally clicking on a suspicious link, an employee immediately contacts the IT helpdesk, allowing the security team to contain any potential threat quickly. |
Covering these areas doesn’t just tick a box; it builds a layered, robust defence where your people are your greatest asset, not your weakest link.
Ensuring Secure Data Handling and Physical Security
In any professional services business, your data is your most valuable asset. That means your training needs to cover the entire journey of sensitive information, from the moment it's created to the day it's securely destroyed. This isn’t just about what happens on-screen, either; security extends to the physical world around us. To get the full picture, it's worth understanding the importance of IT security policies and procedures, as these are the formal rules that guide your team's actions.
Security isn't confined to a screen. A sensitive document left on a printer, an unlocked computer in an empty office, or a casual chat about a client in a public café can all spiral into a serious data leak.
Your training programme has to include practical guidance on:
- Data Classification: Teaching staff how to instinctively tell the difference between public, internal, and highly confidential information.
- Secure File Transfer: Providing crystal-clear instructions on approved ways to share client data—and which tools (like personal cloud storage) to avoid at all costs.
- Clean Desk Policy: Making it second nature for everyone to secure physical documents and lock their computer screens when they step away.
- Removable Media: Highlighting the very real dangers of using unauthorised USB sticks and other portable drives.
Practical Example: A project manager is hot-desking at a client’s site and leaves their laptop unlocked while they grab a coffee. Someone walking past glances at the screen and sees an open proposal, complete with financial projections and strategic plans. That simple lapse is a major data breach, violating client confidentiality and potentially GDPR. Good IT security awareness training drills in the simple muscle memory of hitting Win + L to lock the screen—a two-second action that prevents this exact disaster.
Choosing the Right UK Training Provider

Selecting a partner for your IT security awareness training is a critical decision, one that will directly shape how successful the programme is. The UK market is full of choices, from basic, one-off courses to comprehensive, ongoing training platforms. To make the right call, you need to look beyond the price and consider which approach will actually build a lasting security culture within your business.
It’s a bit like choosing a health and safety plan for your office. You could run a single first-aid course every few years. While that ticks a box, how much will your team truly remember in an emergency a year down the line? A better approach is an ongoing wellness programme with regular workshops and active engagement, making well-being part of the company’s DNA. The same logic applies to cyber security.
A one-time training session might satisfy a compliance requirement, but it rarely changes behaviour for good. A continuous, interactive programme is far more effective at weaving security into daily work, turning it from an annual chore into a shared responsibility.
Key Criteria for Evaluating UK Providers
As you start looking at potential partners, it’s crucial to have a clear checklist. Not all programmes are created equal. What works for a large London corporation probably won’t be the right fit for a professional services firm in Dorset. The goal is to find a provider whose content and delivery style match your unique operational needs.
Focus your evaluation on these key areas:
- UK-Specific Content: Does the material address UK regulations like GDPR? Does it use language and examples that will resonate with a British workforce?
- Engagement Method: Is the training genuinely interactive? Look for quizzes, videos, and real-world scenarios, not just passive "click-next" modules that people forget instantly.
- Phishing Simulations: A must-have. Does the provider offer regular, realistic phishing tests to measure how well employees are doing and keep their detection skills sharp?
- Reporting and Analytics: Can you easily track who has completed the training? Can you spot high-risk individuals or departments and clearly demonstrate improvement over time?
Comparing Training Models and Costs
The training model you select will hinge on your budget and your long-term security ambitions. For instance, the UK government’s National Cyber Security Centre (NCSC) offers high-quality, certified security awareness training that covers the essentials. However, these are often one-off sessions, which can lead to knowledge fading over time.
On the other hand, specialised companies often provide continuous training that adapts to new threats, like QR code phishing, and reinforces learning with regular simulations. While these ongoing services cost more, they deliver a much greater improvement in long-term vigilance and engagement. It’s worth exploring the different UK training providers and their approaches from Guardey.com to get a better sense of what's out there.
Choosing a provider is about finding the right balance. An inexpensive, tick-box solution may feel like a win, but an engaging, continuous programme is an investment that delivers a far greater return in genuine risk reduction.
Ultimately, the best IT security awareness training provider is one who becomes a true partner in your security journey. They should help you build not just knowledge, but a proactive and resilient security culture from the ground up.
Measuring the ROI of Your Training Investment
Every business expense has to answer one fundamental question: what’s the return on investment? When it comes to IT security awareness training, it is crucial for leaders to see it not as a cost but as a strategic investment that delivers real, measurable value. It’s about more than just ticking a compliance box; it’s about tracking key performance indicators (KPIs) that have a direct impact on your bottom line.
The goal is to draw a clear line between a well-trained workforce and a more stable, trusted, and profitable company. When you invest in your people's security skills, you're directly strengthening the resilience of your entire organisation. This shift in thinking is key to showing that effective training is one of the most powerful business tools you have.
Identifying Your Key Performance Indicators
To prove the training is worth it, you need to track the right metrics. These KPIs should be clear, measurable, and tied directly to the secure habits you want to build. Think of them as the vital signs of your company’s security health.
Here are some of the most effective metrics to keep an eye on:
- Phishing Simulation Click-Rates: This is your most direct measure of success. Track the percentage of employees who click on links in simulated phishing emails. Seeing this number steadily decrease over time is a clear signal that the training is hitting home.
- Incident Reporting Rates: It might sound counterintuitive, but an increase in employees reporting suspicious emails is a fantastic sign. It shows they are engaged, vigilant, and know exactly what to do when they spot something questionable.
- Knowledge Assessment Scores: Use quick quizzes before and after training modules to gauge knowledge retention. Better scores show that your team isn't just going through the motions—they're actually understanding the core principles.
Measuring ROI isn't just about the threats you avoid; it's also about the positive behaviours you create. A rise in reported incidents doesn't mean you have more problems—it means your team has become a highly effective human sensor network, spotting threats that automated tools might miss.
Connecting Metrics to Bottom-Line Impact
Once you have your operational metrics, the next step is connecting them to tangible business outcomes. The economic and operational impacts really highlight why security awareness training is so important for UK organisations. In fact, some reports show that companies with structured cybersecurity training can achieve significantly higher income per employee compared to those without it. This underscores the very real business benefits of investing in your team's security skills.
On the other hand, a lack of training is often a common thread in expensive security incidents that cause chaos for operations and damage reputations. These events prove that good training goes beyond compliance; it can prevent serious financial loss, operational downtime, and legal headaches.
For example, a 20% reduction in phishing clicks isn't just a number. It translates into a much lower probability of a ransomware attack, which could save your business tens of thousands of pounds in recovery costs and lost revenue. Similarly, faster incident reporting lets your IT team contain threats before they spread, dramatically reducing the chance of a major data breach and the huge regulatory fines that come with it. For business leaders, it's natural to wonder about the scale of these threats and how concerned you should be about cyber attacks.
A Practical Framework for ROI Calculation
While putting an exact figure on a disaster you prevented is tricky, you can still build a very strong business case. A simple framework can help spell out the value clearly.
- Calculate Training Cost: First, add up the total cost of the training programme. Remember to include platform fees and the cost of employee time.
- Estimate Potential Loss: Next, identify the potential cost of a common incident, like a business email compromise scam or a minor data breach. Factor in everything from data recovery and regulatory fines to lost productivity.
- Demonstrate Risk Reduction: Finally, use your KPIs to show how training has lowered the likelihood of that incident happening. A 50% improvement in phishing resilience means you've literally cut the risk from that attack method in half.
This framework changes the conversation from "How much does training cost?" to "How much risk are we neutralising for this investment?". To dig deeper into the numbers and justify your budget, you can explore additional resources on measuring the ROI on training. This gives you a clear, defensible way to prove that IT security awareness training is a high-return investment in your business’s future.
Best Practices for Effective Programme Implementation
Moving from a plan on paper to a living, breathing programme is where the real work begins. A successful IT security awareness training programme isn't something you just launch and forget; it needs to be woven into the very fabric of your company culture. The aim is to create an environment where people feel empowered and responsible, not watched and scrutinised.
This is all about shifting your mindset. Instead of a one-off, box-ticking exercise, think of it as a continuous, supportive journey. When you get this right, security awareness becomes a shared responsibility that protects everyone. These best practices are your roadmap for turning security plans into tangible, everyday habits.
Secure Buy-In from Senior Leadership
If you want an awareness initiative to stick, it absolutely must have champions at the top. When senior leaders visibly and vocally support the training, it sends a crystal-clear message to everyone else: this matters. Their involvement shows that security is a core business value, not just another problem for the IT department to solve.
Here are a few practical ways to get them involved:
- Have a director or senior partner kick off the training programme with a short video or message.
- Make sure leadership participates in the exact same training modules as everyone else.
- Ask them to mention security successes and ongoing efforts in company-wide meetings.
This kind of endorsement can completely change the perception of the programme, turning it from a mandatory chore into a collective mission. You’ll see engagement and commitment go through the roof.
Integrate Training into the Employee Lifecycle
Security awareness cannot be a one-time event. To build secure habits that last, you need to embed training into the entire employee journey, from their first day to their last. It should be a standard, non-negotiable part of how you operate.
Think about integrating it at these key moments:
- New Employee Onboarding: This is your first and best chance to set expectations. Include a foundational security module as a core part of the induction for every single new hire.
- Regular, Ongoing Training: Supplement that initial training with continuous, bite-sized learning. Monthly or quarterly modules keep security top-of-mind without overwhelming people.
- Annual Refreshers: Once a year, it is wise to review the core principles and introduce new threats to keep everyone’s knowledge up to date.
Foster a Positive Security Culture
The most effective security programmes run on trust and positive reinforcement, not fear and blame. When someone makes a mistake—and they will—like clicking on a phishing link, it must be treated as a learning opportunity. A punitive culture only makes people afraid to report mistakes, driving them underground where they can fester and cause far more damage.
A positive security culture is all about rewarding the right behaviour. When an employee spots a suspicious email and reports it correctly, praise them publicly. This simple act of recognition encourages others to do the same, slowly building a vigilant and proactive human firewall.
Of course, for any awareness programme to land, you have to communicate it well. Consider developing a robust internal communications plan to make sure your training messages are heard and understood by everyone. This helps build the positive momentum you need for a genuine cultural shift.
Finally, make it incredibly easy for people to do the right thing. You need a simple, clearly communicated way for them to report security incidents. Whether it’s a dedicated email address or a one-click button in their inbox, the process should be frictionless. The easier you make it to report a potential threat, the more likely your team is to do it. That small change can be the difference between catching an attack early and dealing with a major breach.
Frequently Asked Questions
When it comes to rolling out IT security awareness training, it's natural for questions to pop up. Getting clear on the practical side of things is what helps UK businesses move from considering a programme to confidently implementing one.
Let's tackle some of the most common questions we hear from decision-makers, especially those in professional services.
How Often Should We Conduct Training?
Think of security training as an ongoing conversation, not a one-time lecture. For any new starter, a solid onboarding session is non-negotiable; it sets the right security-first tone from their very first day.
After that, the key is consistency. We find that short, sharp training modules delivered monthly or quarterly work best. This keeps security fresh in everyone's mind without becoming overwhelming. To really put that knowledge to the test, you will want to run frequent simulated phishing attacks. Round it all off with a comprehensive annual refresher to cover new threats and reinforce the core principles. It is this steady rhythm that builds a genuinely security-aware culture.
Security awareness is not a destination, but an ongoing journey. Consistent, regular engagement is what transforms knowledge into instinct, creating a workforce that is perpetually vigilant against evolving cyber threats.
Our Business Is Small – Do We Really Need This?
Yes, absolutely. It is a common misconception that cybercriminals only go after the big fish. In reality, they often see small and medium-sized businesses (SMBs) as softer targets, assuming they have fewer defences and less to spend on security.
For a smaller professional services firm, the fallout from a single data breach—both financially and in terms of reputation—can be devastating. That’s why IT security awareness training is one of the smartest, most cost-effective security measures you can implement. It’s not about buying expensive, complex technology; it’s about turning your team into your most valuable defensive asset.
How Do We Get Employees to Take It Seriously?
This is the million-pound question, and the answer comes down to engagement. If you want your team to buy in, the training cannot be a dry, box-ticking exercise. It needs to feel relevant to their day-to-day jobs and the specific risks your industry faces. Think interactive quizzes, short videos, and relatable, real-world examples.
Culture is also a massive piece of the puzzle. You get much better results by creating a positive environment where people are praised for spotting and reporting a suspicious email, rather than being punished for making a mistake. When the leadership team visibly champions and participates in the training, it sends a powerful message that this matters to everyone. If you can show your staff how these skills protect their personal data too, you will find they become much more willing partners in defending the business.
Ready to transform your employees into your strongest line of defence? SES Computers provides expert IT security awareness training tailored for businesses across Dorset, Hampshire, and the surrounding areas. We help you build a resilient security culture from the ground up. Protect your business by visiting our website.