A UK Business Guide to Phishing Attack Prevention
Before we dive into how to stop phishing attacks, it’s crucial to get a real sense of what’s at stake. These aren't just nuisance emails we're talking about. They are sophisticated, calculated attempts to exploit the single most vulnerable part of any business's security: its people. A successful attack can lead to significant data breaches, crippling financial loss, and long-term damage to your hard-earned reputation.
The Real Cost of Phishing for UK Businesses

For a professional services firm, the fallout from a phishing incident goes way beyond a single compromised inbox. The true cost is measured in shattered client trust, operational chaos, and the potential for hefty regulatory fines.
Picture this practical example: an employee in your accounts department receives an email that looks like a genuine invoice from a regular supplier. They’re busy, it looks legitimate, and they make the payment. Except, the bank details were changed. Thousands of pounds are gone in an instant. The direct financial hit is bad enough, but the reputational harm and potential ICO fines for the associated data breach can be utterly catastrophic.
Common Tactics to Watch Out For
Cybercriminals aren't just firing off generic spam anymore. Their methods are becoming increasingly targeted and designed to slip past standard security filters by manipulating busy, well-meaning professionals. Recognising these tactics is the first step in building a solid defence.
Here’s a look at some of the most prevalent phishing techniques targeting UK businesses today.
| Attack Type | Primary Target | Key Red Flag | Practical Example |
|---|---|---|---|
| Spear Phishing | Specific individuals (e.g., paralegals, account managers) | Highly personalised content referencing real projects or colleagues. | An email to a junior solicitor mentions a specific case file and asks them to review a "new document" via a malicious link. |
| Whaling | Senior executives (e.g., CEO, CFO, Directors) | Urgent requests for wire transfers or sensitive data, often using authority to rush the target. | A spoofed email from the CEO to the finance director, sent at 5 PM on a Friday, demanding an immediate payment to a "new contractor" to close a deal. |
| Business Email Compromise (BEC) | Finance and accounts payable teams | A sudden, unexpected change in payment details from a known supplier. | An email, appearing to be from a long-standing supplier, informs the accounts team that "due to an audit" they must use new bank details for the next payment run. |
| Smishing & Vishing | Any employee with a company mobile phone | Unsolicited text messages or phone calls creating a false sense of urgency (e.g., from a bank or IT support). | A text message to an employee's work mobile claims their Microsoft 365 account has been locked and directs them to call a fraudulent "helpdesk" number to unlock it. |
These aren't just isolated incidents; they're happening to businesses of all sizes, every single day. Understanding what these attacks look like in the wild is vital for your team.
Phishing is far more than a simple IT problem. It's a critical business risk that directly threatens your financial stability and the trust you've built with your clients. One careless click can undo years of hard work.
And this isn't a hypothetical threat. In the UK, phishing continues to be the most common cyber attack vector by a long shot. The latest government data reveals a staggering 85% of businesses that suffered a breach pointed to phishing as the cause. You can dig into the full report in the Cyber Security Breaches Survey 2024.
This stark reality makes one thing clear: having a robust strategy to prevent phishing isn’t just a good idea—it’s an essential part of doing business today.
Building Your Technical First Line of Defence

While training your team is absolutely vital, your anti-phishing strategy has to start with solid technical controls. These tools are your digital gatekeepers, filtering out the overwhelming majority of threats before they ever land in someone's inbox. Think of it as reinforcing the castle walls before you train the sentries.
Modern email filtering services are far more sophisticated than a basic spam folder. They are your first, and most critical, line of defence. When choosing a solution, you need to look for specific features designed to combat today's advanced phishing tactics.
Here are some practical capabilities to check for:
- Attachment Sandboxing: This is a clever one. It opens email attachments in a secure, isolated environment to see what they do. If there’s any malicious behaviour, it’s contained and never reaches your network. For instance, a seemingly harmless PDF invoice is opened in the sandbox and attempts to run a malicious script; the filter blocks it before your user ever sees it.
- Real-time Link Analysis: Some links are clean when an email is sent but become malicious later. This feature re-scans a link’s destination at the moment of the click, providing up-to-the-second protection. An employee clicks a link that was safe an hour ago, but it now redirects to a fake login page; the filter blocks access in real-time.
- Impersonation Protection: Advanced filters can now use AI to spot the subtle clues of impersonation, like an email that looks like it's from your CEO but has a slightly 'off' tone or originates from an unusual source.
The Undeniable Power of Multi-Factor Authentication
If you do only one thing on this list, make it multi-factor authentication (MFA). It's that important. MFA simply requires a second form of verification – like a code from a mobile app or a fingerprint – on top of a password. This single step is incredibly effective at shutting down account takeovers.
Here’s a classic real-world scenario we've seen play out: an accountant at a small firm gets duped by a clever phishing email and types their Microsoft 365 credentials into a fake login page. The criminals now have the password. But when they try to log in, they're immediately hit with the MFA prompt. Without the accountant's phone to approve the login, that stolen password is now completely worthless. The breach is stopped dead.
MFA single-handedly neutralises the biggest threat of a successful phish—a compromised password. It is the single most impactful technical measure any business can implement for an immediate, dramatic security improvement.
Blocking Threats Beyond the Inbox
A robust defence doesn't end with email. Attackers often use emails to lure people to malicious websites built to steal credentials or drop malware onto their computers. This is where web filtering earns its keep.
A web filter acts as a guard for your internet traffic, blocking access to known malicious or suspicious websites across your entire business network. For example, if an employee clicks a dodgy link in an email, the web filter simply prevents their browser from connecting to the harmful site, displaying a block page instead. It cuts the attack off before it can do any damage and works hand-in-hand with your email security.
Finally, keeping all your software updated is non-negotiable. This means everything—your operating systems, web browsers, and business applications. Cybercriminals are constantly looking for and exploiting known security holes in out-of-date software. Regular updates patch these vulnerabilities, effectively locking the doors that attackers rely on. For a closer look at these foundational security measures, our guide on cyber security for small businesses offers more practical advice.
Building Your Human Firewall: More Than Just a Tick-Box Exercise
While your technical defences are your gatekeepers, they can't catch everything. It's inevitable that a well-disguised phishing email will eventually slip through and land in an employee’s inbox. What happens next is entirely down to the strength of your most valuable defence against phishing: your people.
Your team can be your weakest link or, with the right approach, your strongest asset. Building an effective "human firewall" means ditching the once-a-year, tick-box training session. Instead, you need to cultivate a permanent culture of security awareness, where being vigilant is simply second nature.
The scale of this issue in the UK really brings the point home. Phishing now accounts for a staggering 93% of all cybercrimes targeting UK businesses. And with 79% of UK firms that suffer a cyber attack pointing to phishing as the culprit, it's clear our employees are standing on the front line. You can dig deeper into these phishing attack trends from AAG IT Services.
From Passive Slideshows to Active Defence
Let’s be honest, nobody learns much from a boring slideshow filled with dos and don'ts. The best training is interactive and practical—it empowers your team rather than just lecturing them. This means moving away from passive learning and towards active, hands-on experience.
A cornerstone of any modern security training programme has to be the simulated phishing campaign. These are controlled, safe exercises where you send realistic but completely harmless phishing emails to your own staff. It’s an incredibly powerful way to test and teach in a real-world context, without any of the real-world risk.
For instance, a practical simulation might involve sending a fake email from a well-known courier service with a link to track a parcel that doesn't exist. The results will quickly show you who clicked the link, giving you a clear, honest picture of where your vulnerabilities lie. This data isn't about pointing fingers; it's a valuable tool for identifying which people or departments might benefit from some extra coaching.
The goal of a phishing simulation isn't to catch people out. It's to give them a safe space to make a mistake, learn from it, and be far better prepared for the real thing. It’s this proactive approach that truly builds resilience.
Alongside simulations, you need regular, interactive training modules. These can be short, engaging online courses that teach staff how to spot the common red flags, such as:
- Dodgy Sender Addresses: Showing them a practical example of how a scammer might use a slightly altered domain name (e.g.,
micros0ft.cominstead ofmicrosoft.com). - Urgent or Threatening Language: Explaining the psychological tricks criminals use to create panic and force a quick, thoughtless reaction.
- Suspicious Links and Attachments: Teaching the simple but vital habit of hovering over links to check the true destination URL before ever clicking.
If you're looking for more guidance on what these programmes should cover, our article on IT security awareness training offers a much deeper dive into building an effective curriculum.
Nurturing a No-Blame Reporting Culture
Perhaps the most critical piece of the puzzle is creating a straightforward, no-blame policy for reporting suspected phishing attempts. Your staff must feel completely comfortable raising the alarm without any fear of getting into trouble, even if they've already clicked something they shouldn't have.
Think about this practical scenario: someone on your finance team gets an urgent email, supposedly from the CEO, demanding an immediate bank transfer to a new supplier. Because they've been trained, they notice the slightly off tone and the unusual email address. Instead of panicking and acting, they follow your reporting procedure and flag it to the IT team.
In that single moment, that employee has just saved the company thousands of pounds and prevented a major security disaster. That is the power of a vigilant, well-supported workforce. It’s why your reporting process needs to be simple, visible, and actively encouraged. Your team isn't just a line of defence; they are the very core of your security strategy.
Developing a Practical Incident Response Plan
Let's be realistic: even with the best defences and the sharpest team, a phishing email will eventually slip through the cracks. It’s a numbers game. When that happens, what you do in those first few critical minutes and hours will be the difference between a minor headache and a full-blown business disaster. That’s why you need a clear, pre-defined plan—not panic.
For a professional services firm, an incident response plan doesn't need to be some hundred-page document that gathers dust. Think of it more as a simple, one-page playbook. It should clearly outline the immediate actions, who does what, and how everyone communicates. This way, your team is working from a script, not scrambling in the dark.
Assembling Your Response Team
Even in a small firm, you need to assign specific jobs for when an incident kicks off. Having a clear chain of command is crucial to prevent confusion when stress levels are high and every second counts.
Your core team could look something like this:
- The Incident Lead: This is typically the business owner or a senior manager. They’re the coordinator, the one who makes the final calls.
- The Technical Point Person: This might be your in-house IT specialist or, more likely, your contact at your managed IT support provider. Their sole focus is on the technical side of things—containing the threat.
- The Communications Lead: This person handles all updates. They keep staff in the loop and, if the situation calls for it, manage any communication with clients or regulators.
When roles are crystal clear, everyone knows their part the moment a problem is flagged.
An incident response plan transforms chaos into a structured process. It's the difference between fighting a fire in a panic and executing a well-rehearsed fire drill.
This visual shows a great workflow for combining simulated testing with training and assessment, which is a vital part of getting your team ready for a real event.
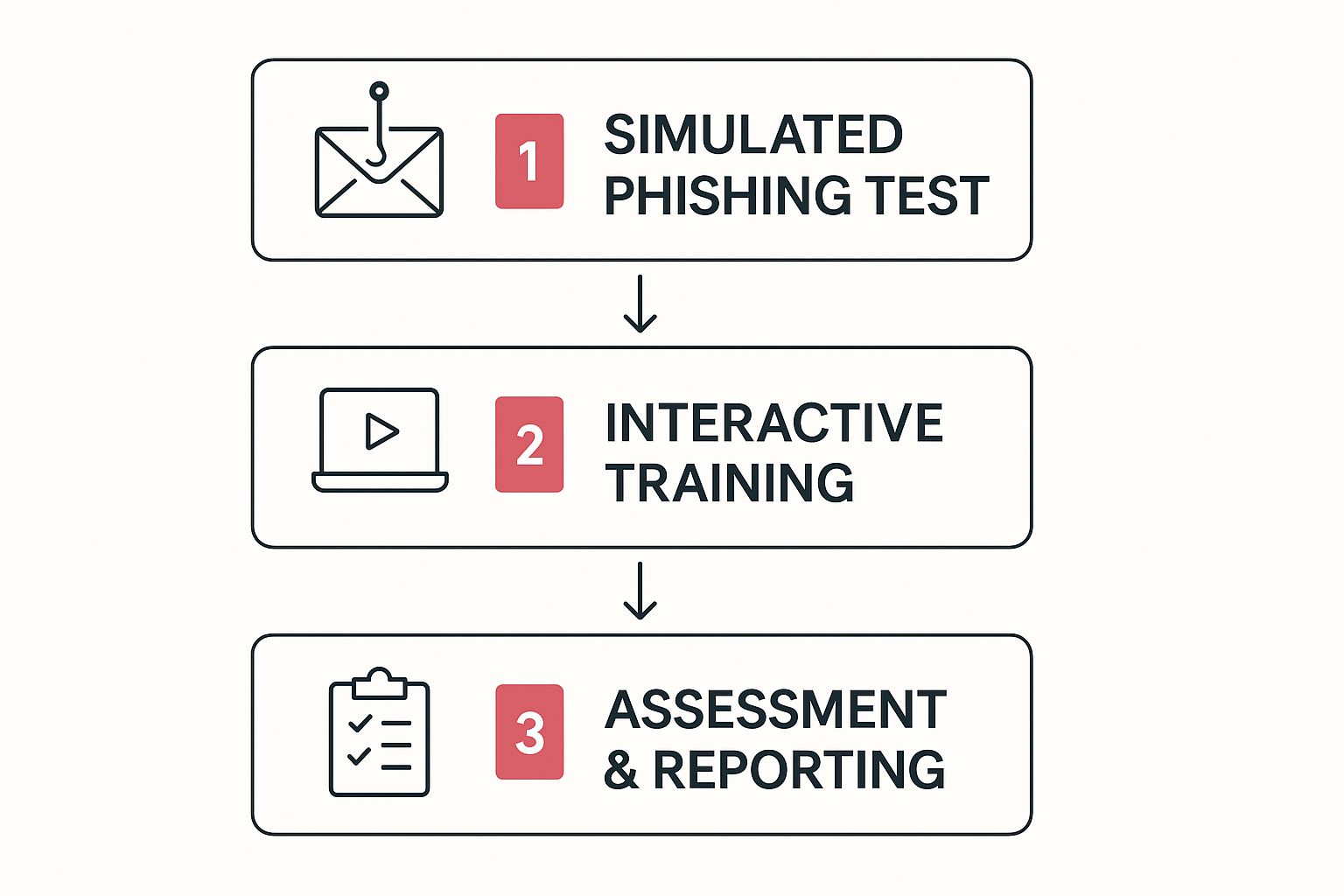
This kind of cyclical process helps reinforce what people have learned and keeps their response skills sharp.
Contain, Eradicate, and Recover
At its heart, your plan should follow a simple framework: minimise the damage and get back to normal as fast as possible. Let’s walk through a practical scenario. An employee in a law firm gets an email that looks like a file request from a client, they click the link, and… uh oh.
Containment – Stop the Bleeding
The first priority is to stop the threat from spreading. You have to act fast.
- Isolate the machine: The very first thing to do is get that employee's computer off the network. Unplug the ethernet cable and switch off the Wi-Fi. Cut its connection to everything else.
- Change compromised passwords: The employee needs to immediately change their email password, plus any other accounts that share the same login details.
- Block malicious indicators: Your IT support team should get to work blocking the sender's email address and the dodgy domain at a network level to stop it from affecting anyone else.
Eradication – Remove the Threat
Once the immediate danger is contained, you need to be sure the threat is completely gone. This isn't just a quick scan; it's a deep dive into the affected device and possibly your whole network to ensure no nasty backdoors have been left behind for later.
Recovery – Get Back to Business
The final phase is all about getting things running again. This means restoring any affected systems and data from clean, recent backups and then keeping a close eye on everything for any further suspicious activity.
Just as importantly, this is your chance to learn. A post-incident review is essential to figure out what went wrong and how you can beef up your defences to prevent it from happening again.
For a more detailed look at these steps, you can explore our guide on what to do after a cyber attack. Knowing this process inside-out means you’re prepared not just to fend off attacks, but to handle them like a pro when one gets through.
Taking Your Defences to the Next Level
Once you’ve got the basics locked down, it’s time to get more proactive. Think of it as moving from just having a strong front door to installing a full-blown security system that actively works to keep threats out. These next steps are about hardening your defences and making your business a much less appealing target for scammers trying to impersonate you.
Lock Down Your Domain with Email Authentication
A huge part of this is implementing email authentication protocols. It might sound a bit techy, but the concept is straightforward: you’re essentially giving other email servers a way to verify that an email actually came from you. It’s the digital equivalent of an official seal on a letter.
There are three key standards you need to know about:
- SPF (Sender Policy Framework): This is basically a public list of all the mail servers you’ve authorised to send emails from your domain. If a message comes from an unlisted server, it’s immediately suspicious.
- DKIM (DomainKeys Identified Mail): Think of this as a tamper-proof seal. It adds a unique digital signature to every email you send, so the receiving server can check that nobody has altered it in transit.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): DMARC is the policy that ties it all together. It tells other servers what to do if an email fails the SPF or DKIM checks – for instance, you can instruct them to reject it outright.
Getting these three set up makes it incredibly difficult for attackers to spoof your domain and trick your clients, partners, or even your own team with fake emails.
Keep an Eye on Emerging Threats
Even with the best authentication in place, you can’t afford to set it and forget it. You need to maintain visibility over your email traffic to spot anything out of the ordinary. Continuous monitoring allows you to catch unusual patterns that could signal an attack in progress, like a sudden flood of emails from an unknown source or a spike in messages with strange attachments. This lets your IT team get ahead of the problem before it becomes a real crisis.
This kind of vigilance is critical, especially when you consider how quickly things are changing. The UK is one of the most targeted countries in the world for these kinds of attacks, with criminals constantly finding new ways to impersonate trusted organisations like HMRC. For a deeper look into this, it’s worth reading up on the latest UK-specific cyberattack trends on Daily Security Review.
Adopting advanced email authentication is like getting a registered trademark for your email domain. It proves you are who you say you are and stops imposters from damaging your company’s reputation.
Getting Ready for AI-Powered Phishing
Looking to the future, the next big challenge is AI. Criminals are already using artificial intelligence to write incredibly convincing, personalised phishing emails at scale. These messages are free of the usual grammar mistakes and can be tailored to an individual by scraping their public information, making them much harder to detect.
So, how do you prepare for this? It’s all about strengthening the defences you already have. Double down on your technical controls like DMARC. Make your employee training even more sophisticated, teaching people to question the context of a request, not just to look for typos. Above all, foster a culture where it’s perfectly normal—and even encouraged—to be a little bit suspicious and double-check any unusual requests. Against these hyper-realistic threats, your team remains your most valuable line of defence.
Common Questions Answered
When you're working to protect your business from phishing, a few questions always seem to pop up. Let’s tackle some of the most common ones we hear from business owners and managers, clearing up any confusion and helping you build a stronger defence.
Are Free Anti-Virus Tools Enough to Stop Phishing Attacks?
In a word, no. While a free anti-virus tool can offer a basic safety net against some well-known malware, it's simply not built for the kind of threats professional services firms face today. Modern phishing scams are clever; they often don't even use a traditional virus. Instead, they rely on social engineering to fool your staff into handing over passwords or authorising dodgy payments.
A professional business needs a security setup with multiple layers. This means having advanced email filters that can check links and attachments in a safe, isolated environment (a 'sandbox'), alongside anti-spoofing technology like DMARC. Sticking with free tools leaves big, expensive holes in your security that attackers are getting very good at finding.
How Often Should We Run Phishing Awareness Training?
Think of security awareness as a continuous commitment, not a one-time box-ticking exercise. A deep-dive training session once a year is a good foundation, but it needs to be backed up with regular, bite-sized reminders to keep security at the front of everyone's mind.
What's even more crucial is running your own simulated phishing tests. Sending these controlled, fake phishing emails to your team—say, every quarter—is one of the best ways to keep them sharp. It helps you see how effective your training is and highlights anyone who might need a bit of extra support. Threats are always changing, so this kind of ongoing education is key to keeping your ‘human firewall’ strong.
The most effective training is a continuous cycle of testing, educating, and re-testing. It builds muscle memory, transforming vigilance from a conscious effort into a natural reflex for your team.
We’re Only a Small Business. Are We Really a Target?
Yes, absolutely. Believing you're too small to be a target is one of the most dangerous assumptions you can make. From a cybercriminal's perspective, small businesses are often the perfect victims because they assume you have fewer security measures in place.
Attackers use automated tools to blast out thousands of phishing emails at once, so your company's size doesn't make you invisible. On top of that, professional services firms are often a stepping stone into the supply chain of larger organisations. This makes you an attractive—and often softer—target for criminals trying to land a bigger fish. Effective phishing attack prevention is just as vital for a ten-person accountancy firm as it is for a global corporation.
At SES Computers, we understand the unique challenges that small and medium-sized businesses face. We offer proactive, multi-layered security solutions and managed IT support to protect your operations from threats like phishing. To build a more resilient defence for your business, explore our managed IT support and security services.