What Is Multi Factor Authentication? Protect Your UK Business
Multi-Factor Authentication (MFA) is a security system that asks you to prove you are who you say you are in more than one way. Think of it like needing both a keycard and a PIN to enter a secure building; a password on its own is just one flimsy lock, and that is no longer enough to guard your business's critical data.
Unlocking the Basics of Multi-Factor Authentication
Picture your company's files locked away in a digital safe. A simple password is the only thing protecting it. If a cybercriminal gets their hands on that one password, they can walk right in and take whatever they want.
Multi-Factor Authentication is all about adding more locks to that safe, with each one needing a completely different kind of key. This layered defence means that even if a thief steals one key (like a phished password), your sensitive information stays protected behind the other locks.
At its core, MFA strengthens your security by requiring proof of identity from at least two different categories. It is a simple but powerful idea: to get in, you need to present multiple, independent credentials that prove it is really you.
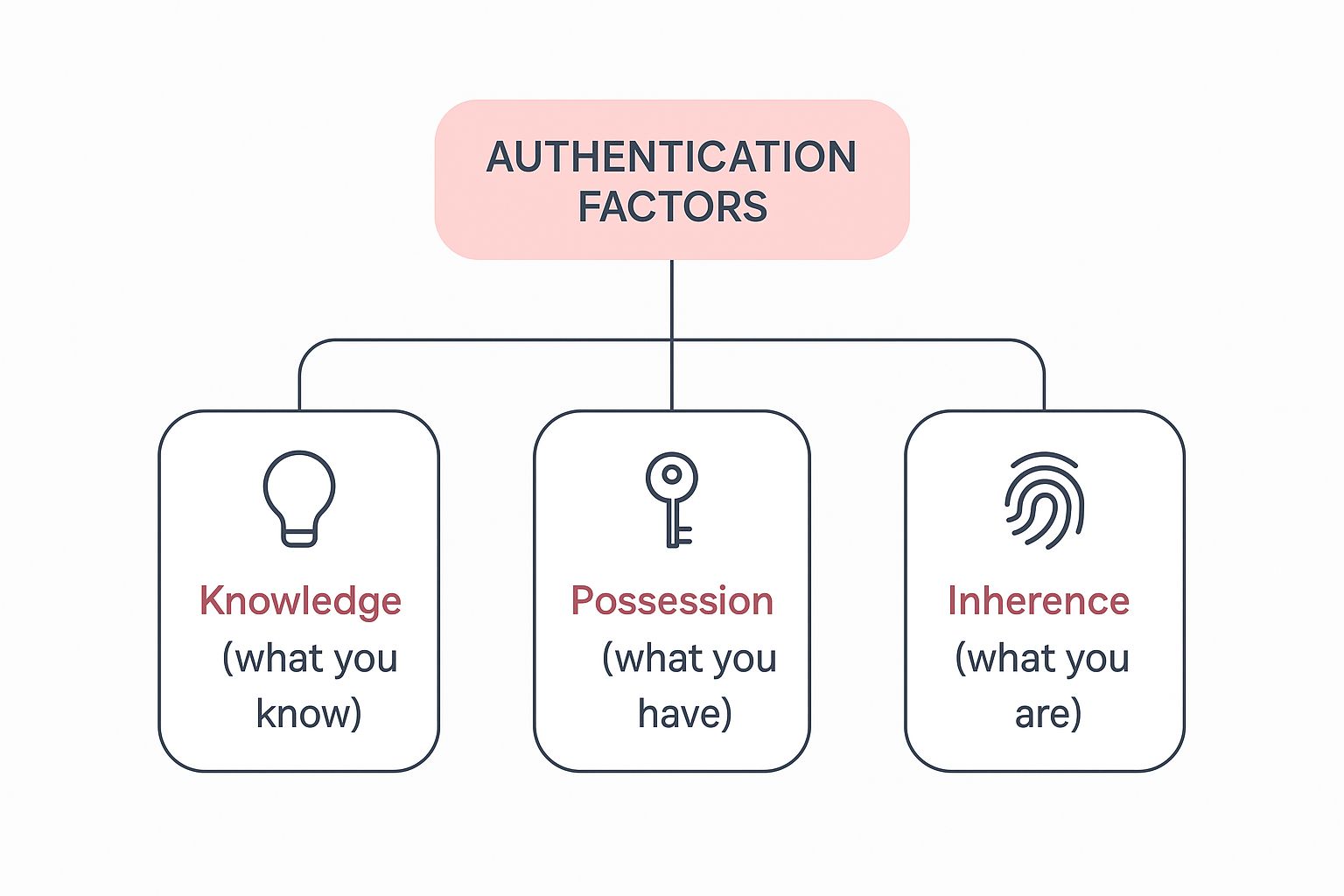
The Three Pillars of Authentication
MFA is built on three distinct types of proof, often called "factors". To successfully log in, you must provide a combination of at least two of these.
Here is a breakdown of the three pillars and how they work in a professional services setting.
| Factor Type | Description | Practical Business Example |
|---|---|---|
| Something You Know | This is information that should only be known by you. It's the most traditional form of verification. | An accountant at a professional services firm enters their unique, complex password to log into the company’s client portal. |
| Something You Have | This involves a physical object you possess. It proves your identity by confirming you have the item with you. | A project manager receives a push notification on their company smartphone and must tap "Approve" before accessing the shared project files on SharePoint. |
| Something You Are | This factor uses your unique biological traits, also known as biometrics, to verify your identity. | A partner at a law firm uses their fingerprint to unlock their work laptop before accessing confidential case files. |
These three pillars work together to create a formidable barrier against unauthorised access.
By combining elements from these different categories, you build a security posture that is exponentially stronger than relying on a password alone.
The "something you are" factor, in particular, is becoming more common. You can learn more about this technology through resources on biometric authentication.
The results of implementing MFA speak for themselves. It is proven to block between 80% to 90% of cyber-attacks. When Google rolled out two-factor authentication to over 150 million users, they saw a staggering 50% drop in account compromises.
This principle of "never trust, always verify" is also a cornerstone of a modern security strategy. You can see how it fits into a broader framework in our guide on what is zero trust security: https://www.sescomputers.com/news/what-is-zero-trust-security/.
Seeing Multi-Factor Authentication in Action
The theory behind Multi-Factor Authentication is all well and good, but seeing it click into place during a normal working day is where you really appreciate its simple genius. Let us take the concept off the page and look at a practical, real-world scenario that is likely familiar to professionals across the UK.
Picture a remote employee, we will call her Sarah, working for a consultancy based in Hampshire. She needs to log into her company’s cloud-based project management tool to check on sensitive client data. This everyday task is the perfect moment to see how MFA adds a powerful security layer without getting in the way.
First, Sarah opens the login page and enters her username and password. This is the first factor – something she knows. It is the standard first step we're all used to, but with MFA in place, it is no longer the only step.

The instant she hits ‘enter’ on her password, the system triggers the second factor. A push notification pops up on her company-issued smartphone, a device that has been specifically registered to her account. This is something she has. The notification asks a simple question: "Approve this sign-in attempt?" Sarah taps "Approve," and that is it. She is in.
This entire process, often lasting just a few seconds, confirms her identity by combining what she knows (her password) with what she has (her phone). It is an incredibly effective way to block anyone who might have managed to steal her password but doesn't have her device.
Comparing Common MFA Methods
While push notifications are incredibly popular for being so slick and easy, they are just one of several great MFA methods. The right choice for your business really comes down to finding the sweet spot between user-friendliness and the level of security you need.
Let us see how Sarah’s experience would change with other common approaches:
- Authenticator Apps (like Google Authenticator): Instead of a push notification, Sarah would open an app on her phone. This app would show a six-digit code that changes every 30 seconds. She would simply type that code into the login screen to get access. This is a very secure method because the codes are generated offline. For a professional services firm, this is ideal for securing access to cloud accounting software like Xero.
- SMS Text Message Codes: The system would send a one-time code as a text message to Sarah’s mobile. It is a widely used and accessible option. However, it is generally considered less secure than an authenticator app due to a niche but real risk called "SIM-swapping." Some services even provide temporary phone numbers for SMS verification to demonstrate this type of workflow.
- Physical Security Keys: For maximum-security environments, Sarah might be given a small USB device. After putting in her password, she would plug this key into her computer and tap it. This physical action proves it is her, making it nearly impossible for a remote attacker to break in. This method is often used by system administrators to protect access to critical network infrastructure.
Each one of these methods successfully layers different factors to prove someone is who they say they are. The crucial thing for any business owner to realise is that modern MFA is not the clunky, frustrating process it once was. It is designed to fit smoothly into your team’s daily routine, delivering powerful protection that feels almost effortless.
Why MFA Is a Game Changer for UK SMEs
For small and medium-sized businesses in the UK, cybersecurity can often feel like an overwhelming and expensive puzzle. But thinking of Multi-Factor Authentication as just another IT cost is a mistake. It is one of the smartest commercial decisions you can make—one that directly protects your revenue, reputation, and future growth.

Putting MFA in place is a powerful investment in business resilience. It shifts your security from a reactive, "what-if" stance to a proactive one, safeguarding your operations and keeping the business running smoothly, even in the face of an attack.
Protecting Your Business and Reputation
Every business owner worries about data breaches. The fallout isn't just about the immediate financial hit; it is about the potential for crippling GDPR fines and the lasting damage to a reputation you've worked tirelessly to build. A single stolen password could be all it takes for a criminal to get their hands on everything from client lists to private financial records.
Think of MFA as your digital bouncer. It dramatically shrinks the chance of a successful breach because even if a password is stolen, it is essentially useless on its own.
For an SME, trust is everything. When a client hands over their data, they are placing their confidence in you. Having robust security like MFA in place is a clear signal that you take that responsibility seriously.
This commitment to security quickly becomes a competitive edge. In a crowded marketplace, being the business that can confidently tell clients their information is safe helps you stand out. It can even be the deciding factor in winning contracts, particularly with larger organisations that have their own strict security standards.
Enabling Secure and Flexible Operations
The days of everyone working from a single office are long gone. For many UK businesses, flexible and remote working is now the norm, boosting productivity and keeping staff happy. The downside? This new freedom brings new security headaches.
MFA is the essential foundation for secure remote work. It verifies that only authorised team members can access company networks and apps, no matter where they are or what device they are using. This is what allows your team to work effectively and safely, whether they are in a home office in Hampshire or on-site with a client in Dorset.
Unfortunately, far too many businesses remain vulnerable. The UK's Cyber Security Breaches Survey revealed that while 43% of UK businesses reported a cyber security breach, the adoption of basic defences is worryingly low. In fact, a staggering 62% of small and mid-sized firms do not require MFA, leaving a massive security gap. You can explore more of these multi-factor authentication statistics on JumpCloud. By implementing MFA, you immediately place your business in the more secure, resilient minority, ready to thrive.
How to Choose and Roll Out Your MFA Solution
Picking the right Multi-Factor Authentication system and getting it running smoothly is one of the most important security decisions you will make. The real goal here isn’t just to tick a security box; it is to find a solution that fits neatly into your existing workflow, plays well with software like Microsoft 365, and provides serious protection without driving your team mad.
A successful rollout is all about that balance between robust security and a frictionless user experience.

This isn't a niche concern anymore. It is rapidly becoming the standard. The global MFA market, valued at around $14.4 billion, is expected to nearly double in the coming years. Here in the UK, the shift has been dramatic, with business adoption rocketing from 28% to 78% in a single year. This isn't just a trend; it is a fundamental change driven by new compliance rules and rising industry standards. You can dig deeper into these figures and explore the growth of multi-factor authentication on scoop.market.us.
To make the right choice, you first need to take a good, hard look at your own business environment and the specific risks you face.
Evaluating Your Business Needs
Before you start looking at fancy tools and features, you need a crystal-clear picture of what you are protecting and how your team actually gets their work done. Diving in too quickly often leads to user friction and poor adoption, which completely defeats the purpose of the exercise.
Start by asking a few straightforward questions:
- What software are we protecting? Make a simple list of your business-critical applications. This will include your email platform (like Microsoft 365), any accounting software you use, and crucial client databases. Your MFA solution absolutely must be compatible with these systems.
- What is our team’s technical comfort level? Be honest about this. A team that isn't particularly tech-savvy will likely find simple push notifications on their phones far easier to manage than copying and pasting codes from an authenticator app.
- What is our real risk profile? A law firm handling highly sensitive client data might need the uncompromising security of a physical token. On the other hand, a small marketing agency with lower-risk data could be perfectly secure using app-based authenticators.
Your goal isn't to find the most complex, Fort Knox-style MFA system. It is to find the most effective one for your unique situation. The best solution is always the one your team will actually use, every single day.
Comparison of Common MFA Implementation Methods
With a clear understanding of your needs, you can start comparing the different ways to implement MFA. Each method strikes a different balance between security, user convenience, and cost, so it helps to see them side-by-side.
This table breaks down the most popular options available today.
| Method | Security Level | User Convenience | Typical Use Case for Professional Services |
|---|---|---|---|
| Authenticator App | High | High | A fantastic all-rounder, ideal for securing cloud apps like Microsoft 365 and client management systems. |
| Physical Security Key | Very High | Medium | The best choice for protecting high-privilege accounts, such as for partners or IT administrators accessing sensitive financial or legal records. |
| Biometrics (Fingerprint/Face ID) | High | Very High | Perfect for securing company-issued devices like laptops and smartphones, offering a seamless and quick user experience for fee-earners. |
| SMS/Email Codes | Standard | High | A solid entry-level option, but it is the least secure method and is vulnerable to attacks like SIM-swapping. |
While an authenticator app often hits the sweet spot for many small businesses, do not rule out using a mix of methods. You might, for example, use biometrics for device access and a physical key for your main administrator account.
A Roadmap for a Smooth Rollout
Let's be clear: a successful implementation is more about people than it is about technology. A well-thought-out plan ensures your team understands why this change is happening, feels supported through the process, and adopts the new security habit with confidence.
- Craft a Clear Communication Plan: Do not just fire off an email announcing that MFA is now mandatory. Take the time to explain why you're doing this. Frame it as a benefit that protects the business, their work, and even their personal information.
- Launch a Pilot Programme: Before you flip the switch for everyone, test the system with a small, tech-friendly group. This is your chance to iron out any technical wrinkles or user experience snags in a low-stakes environment.
- Provide Practical Training and Support: Run a short, hands-on training session to walk everyone through the setup. More importantly, make sure they know exactly who to contact for help if they get stuck, lose their phone, or misplace a security key.
- Establish Ongoing Management: Your work isn't done after launch day. You need a clear process for enrolling new starters and for helping existing staff who get locked out. A responsive and helpful support system is absolutely crucial for long-term success.
Overcoming Common Hurdles in MFA Adoption
Rolling out any new technology can feel like an uphill battle, often met with a mix of questions and resistance. When it comes to Multi-Factor Authentication, a few common myths can stop UK businesses from making this crucial security upgrade. But these hurdles are almost always built on outdated ideas of how MFA actually works.
By tackling these concerns head-on with clear communication and a good plan, you can make the transition a smooth one. The goal is to show your team that MFA is not a complicated roadblock; it is a simple tool that protects them, their work, and the entire company from very real threats.
Myth 1: MFA Is Too Complicated for My Team
One of the first worries I hear from business owners is that MFA will confuse their staff and grind productivity to a halt. The truth is, modern MFA is the complete opposite. Many systems today rely on simple push notifications—a single tap on a smartphone is all it takes to approve a login.
Honestly, that is often quicker and far less hassle than typing out a long, complex password. To make the rollout even smoother, a bit of planning goes a long way. This means providing some focused training to show everyone just how straightforward the new process really is. Investing in proper IT security awareness training builds confidence and ensures the team understands not just how to use MFA, but why it is so important.
The goal isn’t to add friction; it's to create a secure habit. A brief, hands-on session can quickly turn anxiety into confidence, proving that MFA is a simple, powerful safeguard.
Myth 2: It Is Too Expensive for a Small Business
Another major roadblock for many SMEs is the perceived cost. The good news is that implementing strong MFA does not have to break the bank. In fact, for a lot of businesses, it can be completely free.
Chances are, powerful MFA features are already built into the professional software you use every single day.
- Microsoft 365: If your business runs on Microsoft services, robust MFA options are included right out of the box, just waiting to be switched on.
- Google Workspace: It is the same story with Google. Strong authentication features are already part of its business suite at no extra cost.
- Third-Party Apps: Plenty of free authenticator apps, like Google Authenticator or Microsoft Authenticator, provide a high level of security without charging a penny.
By looking at the tools you already pay for, you can seriously strengthen your security with little to no extra investment. This makes MFA one of the most cost-effective security upgrades any business can make, delivering a massive return in risk reduction.
Taking Your First Steps Towards Better Security
We've covered a lot of ground in this guide, establishing that multi-factor authentication is one of the most powerful and accessible security upgrades any modern UK business can make. Now, it is time to put that knowledge into practice.
Protecting your business, your clients, and the reputation you have worked so hard to build starts with this simple, foundational layer of security. The threat of a data breach is always there, but your defence does not have to be complicated. Implementing MFA is the single most effective step you can take to stop the overwhelming majority of cyber-attacks dead in their tracks.
Do not wait for a security incident to force your hand. Being proactive with MFA shows a real commitment to security, which is something that builds client trust and keeps your business running smoothly. Think of it as a strategic investment in your company's future.
Your journey to better security can start today with a few straightforward actions:
- Assess Your Critical Systems: First, pinpoint which applications house your most sensitive information. This could be your email platform, your client database, or your financial software.
- Review Existing Tools: Take a look at the software you already use. Many platforms, like Microsoft 365, have built-in MFA features that you might just need to switch on.
- Plan Your Rollout: Map out a clear communication and training plan. This will help your team understand the change and adopt the new process with confidence.
A proper review is the best place to begin. To help you identify your priorities and what to look for, our comprehensive cyber security audit checklist is a brilliant resource.
Your MFA Questions Answered
Even when you grasp the basics of Multi-Factor Authentication, a few practical questions always seem to pop up for UK business owners. Let's tackle some of the most common ones to help you make smarter security decisions.
What's the Real Difference Between 2FA and MFA?
Think of it like this: MFA is the overall strategy, and Two-Factor Authentication (2FA) is just one way—albeit a very popular one—to execute it.
The names themselves are the biggest clue:
- Two-Factor Authentication (2FA) requires exactly two different proofs of identity. A classic example is your password plus a one-time code sent to your phone.
- Multi-Factor Authentication (MFA) is the wider term for any system that requires two or more proofs.
So, all 2FA is a type of MFA, but not all MFA is limited to just two factors. You could, for instance, have a system that requires a password, a fingerprint, and a security key. That would be MFA, but not 2FA.
Can Hackers Actually Get Past MFA?
Let's be realistic: no security measure is a silver bullet against a determined, well-funded attacker. However, MFA is incredibly effective at slamming the door on the most common threats that businesses face every day.
Automated attacks like credential stuffing, where criminals try thousands of stolen passwords at once, are stopped dead in their tracks by MFA. Your password could be all over the dark web, but without that second factor, the bots cannot get in.
It is crucial to remember that some MFA methods are stronger than others. SMS codes are a great first step, but they can be intercepted by a clever scam known as 'SIM-swapping'.
For truly robust protection, you will want to move beyond texts. Using an authenticator app or a physical security key raises the bar significantly, making it exceptionally difficult for an attacker to compromise your account.
What's the Cost of MFA for a Small Business?
This is the best part—implementing MFA can cost anywhere from absolutely nothing to a very small per-user, per-month fee. Its affordability is one of its biggest advantages for small businesses.
Chances are, the tools you already use every day have powerful MFA features built right in. Major platforms like Microsoft 365 and Google Workspace include robust MFA options as standard with their business plans.
This means you can dramatically strengthen your security without adding a single pound to your monthly software bill. It is easily one of the most cost-effective security upgrades any UK business can make.
At SES Computers, we help businesses across Dorset and Hampshire put practical, effective security like MFA in place. To make sure your systems are properly protected, contact us today for a security consultation.