Penetration Testing vs Vulnerability Scanning: UK Business Guide
At the heart of the matter, penetration testing and vulnerability scanning are two very different beasts, each with its own approach and goal. Think of vulnerability scanning as an automated, wide-ranging health check for your systems. It casts a wide net, flagging up a list of potential security weak spots by cross-referencing against massive databases of known issues.
On the other hand, penetration testing is a hands-on, simulated cyber attack. It is a targeted effort by a human expert to actually exploit those potential weaknesses, confirming whether they pose a genuine threat and what the business impact could be. They are not interchangeable; they are two sides of the same coin, both essential for a well-rounded cyber defence.
Choosing Your Cyber Defence Strategy
For any business leader in the UK, getting to grips with what separates a pen test from a vulnerability scan is the first step. It is about making smart, cost-effective decisions to protect your organisation. One does not replace the other; they work in tandem to create layers of security.
Vulnerability scanning is your first line of automated defence—a regular, proactive check-up of your entire IT estate. It is fantastic for catching the common, known problems before they escalate. A penetration test, however, brings a human element into the mix. It mimics the creativity, persistence, and mindset of a real attacker to answer that one critical question: "If we were attacked right now, how would we hold up?"

Defining the Core Differences
To really hammer home how they differ, let’s break it down.
| Criterion | Vulnerability Scanning | Penetration Testing |
|---|---|---|
| Methodology | Automated software scans networks and systems for known flaws. | A manual, human-driven process mimicking a real attacker's tactics. |
| Objective | To identify and list potential vulnerabilities. | To exploit vulnerabilities and determine their real-world impact. |
| Scope | Broad and shallow, covering many assets quickly. | Narrow and deep, focusing on specific targets to find complex flaws. |
| Frequency | High (weekly or monthly) for continuous monitoring. | Low (annually or biannually) for periodic, in-depth validation. |
This distinction is crucial, especially when you consider that around 50% of UK businesses have faced a cyber attack or breach in the last year. Regular vulnerability scans are your baseline for continuous security hygiene, but it is the pen test that gives you the invaluable context of what is truly exploitable and the risk it poses to your business.
A vulnerability scan tells you that a window might be unlocked. A penetration test confirms that a burglar can open that window, get inside, and crack open the safe.
Ultimately, the strongest security programmes weave both practices together. The automated breadth of scanning keeps you on top of day-to-day issues, while the manual depth of a pen test validates your defences against a determined attacker. This layered approach is particularly vital for small and medium-sized businesses, which are increasingly finding themselves in the crosshairs. To build a stronger defence, have a look at our guide on cyber security for small businesses.
How Vulnerability Scanning Works
At its core, vulnerability scanning is like sending out a highly efficient, automated scout to survey your digital territory. It involves using specialised software that systematically probes your systems, networks, and applications, checking them against a massive, constantly updated database of known security weaknesses. You can think of it as a routine, automated security check-up designed to give you a broad overview of your potential exposure.

The primary objective here is breadth over depth. These scanners are programmed to hunt for common and well-documented vulnerabilities—things like unpatched software, weak configurations, or services running on outdated protocols. For example, a scan might quickly identify that a web server is still running an old version of Apache with a known remote code execution flaw. Because it is an automated process, you can run these scans frequently and consistently, making it a fundamental part of any solid cyber hygiene programme. It is the digital equivalent of methodically rattling every door and window in a building to see which ones have been left unlocked.
Types of Vulnerability Scans
To get a complete picture of your security posture, scanning is often broken down into different types. Each offers a unique vantage point, and the right one to use really depends on what part of your infrastructure you are trying to assess.
Here are the most common approaches:
- External Scans: These are launched from outside your network's perimeter, essentially simulating the view an attacker would have from the internet. They focus on your public-facing assets like websites, firewalls, and mail servers to spot any weaknesses visible to the outside world. For example, an external scan would detect if your firewall has port 3389 (Remote Desktop) unnecessarily open to the internet.
- Internal Scans: Conducted from inside your network, these scans are designed to find risks that could be exploited by an insider or by an attacker who has already found a way past your outer defences. They frequently uncover issues with internal patching schedules or misconfigured devices that would not be seen from the outside, such as a file server with incorrect permissions allowing any staff member to access sensitive HR documents.
- Authenticated Scans: For this type of scan, the software is given login credentials, allowing it to sign into the system just like a legitimate user. This "behind-the-curtain" access provides a much more detailed view, highlighting things like weak password policies, software flaws on employee workstations, and incorrect access controls. A practical example would be finding outdated, vulnerable software installed on an employee's laptop that is only visible after logging in.
- Unauthenticated Scans: As the name suggests, these scans operate with no credentials. They provide an attacker's perspective of what can be discovered on your network without any special access, often revealing issues like open ports or default device configurations that have been overlooked. This might flag a newly installed printer still using its factory-default "admin/admin" password.
Interpreting the Scan Output
Once a scan is complete, you will typically receive a detailed report that lists all the issues it found. Each vulnerability is usually assigned a severity rating—such as Critical, High, Medium, or Low—based on a standard framework like the Common Vulnerability Scoring System (CVSS). This system helps your IT team prioritise their efforts, tackling the most dangerous flaws first.
The real challenge with vulnerability scan reports is their lack of context. A scanner might flag a ‘Critical’ vulnerability, but it cannot tell you whether that flaw is actually exploitable in your specific environment. It identifies the ‘what’ but not the ‘how’ or the ‘so what’.
This is a crucial point of difference in the penetration testing vs vulnerability scanning discussion. A scanner provides a list of potential problems but stops short of trying to exploit them. For example, a report might say an application is vulnerable to a known SQL injection attack, but it will not verify if a web application firewall you have in place would actually block that attack. To better understand the importance of identifying these flaws, you can explore the theory and practice behind full disclosure of security vulnerabilities.
Ultimately, this breadth-first approach creates a foundational layer of security, giving you a comprehensive inventory of risks that need further investigation and action.
Simulating a Real-World Cyber Attack
While a vulnerability scan gives you a wide-ranging list of potential weak spots, penetration testing (or pen testing) comes at the problem from a completely different angle. Think of it as a controlled, intelligence-led simulation of a genuine cyber attack. It is driven by human expertise, moving beyond simply finding flaws to actively exploiting them. The goal is not to find every single vulnerability; it is to see if a determined attacker can actually break through your defences and what they could do once inside.
This is not a chaotic, smash-and-grab exercise. Professional ethical hackers follow well-defined frameworks like the Penetration Testing Execution Standard (PTES) to make sure the simulation is thorough, safe, and can be repeated. It is a deep dive that focuses on linking multiple, sometimes minor, vulnerabilities together to reach a specific goal—exactly like a real attacker would. This ‘depth-first’ approach provides a true test of your security controls and your team's ability to respond to an incident.
The Stages of a Simulated Attack
A professional pen test does not happen all at once. It unfolds in a series of logical stages, with each step building on the one before it. This structure ensures every action has a purpose and the final report shows clear, real-world attack paths. It is this process that showcases the creativity and critical thinking that automated tools just cannot match.
A typical test breaks down like this:
- Reconnaissance and Intelligence Gathering: It all starts with gathering as much information as possible about the target organisation. This could mean digging through public records, social media, and data breach dumps to find things like employee names, email address formats, or even old passwords that might still be in use.
- Scanning and Vulnerability Analysis: Here, testers will use a mix of automated tools and manual investigation to identify potential entry points. The key difference from a standard vulnerability scan is that they are specifically looking for weaknesses they believe they can actively exploit.
- Exploitation: This is where theory becomes practice. The ethical hacker attempts to use the vulnerabilities they have found to gain unauthorised access. This hands-on attempt is what truly separates a pen test from a simple scan.
- Post-Exploitation: Once they have a foothold, the tester's job is not done. They will try to escalate their privileges and move deeper into the network. The goal is to see how far an attacker could really get—can they reach sensitive data? Can they set up a persistent presence?
A Practical Pen Test Example
Let’s walk through a scenario to see how this plays out. A penetration tester starts with reconnaissance and discovers that a company's marketing team recently attended a big industry conference. By checking the public attendee list against known data breaches, the tester uncovers an old, leaked password for one of the marketing employees.
Now, the exploitation phase begins. The tester tries this password on the company's cloud email service, and it works. They are in. From there, it is all about post-exploitation. Sifting through the emails, the tester finds a shared document containing login details for an internal server. Using these, they pivot from the cloud into the internal network, and before long, they have accessed a database full of sensitive customer information.
A vulnerability scan might have flagged that the cloud service was not enforcing multi-factor authentication. A penetration test proves how that one oversight could directly lead to a catastrophic breach of customer data, showing the real, tangible business impact.
This story highlights the core value of a pen test. It does not just give you a list of disconnected problems; it weaves a narrative showing how an attacker could string together seemingly low-risk flaws to achieve a high-impact compromise. It provides a clear answer to the critical question every business leader needs to ask: "Are our defences strong enough to stop a skilled and determined attacker?"
Vulnerability Scanning vs Penetration Testing: A Side-by-Side Comparison
To really get to the heart of the penetration testing vs vulnerability scanning debate, we need to look past the basic definitions and get into the practical, day-to-day differences. While both are designed to bolster your company's defences, they are fundamentally different tools for different jobs, each with its own methodology, objective, and outcome.
Think of them as complementary strategies rather than competing ones. One gives you a wide-angle view of your security landscape, while the other provides a deep, focused close-up on your most critical assets.
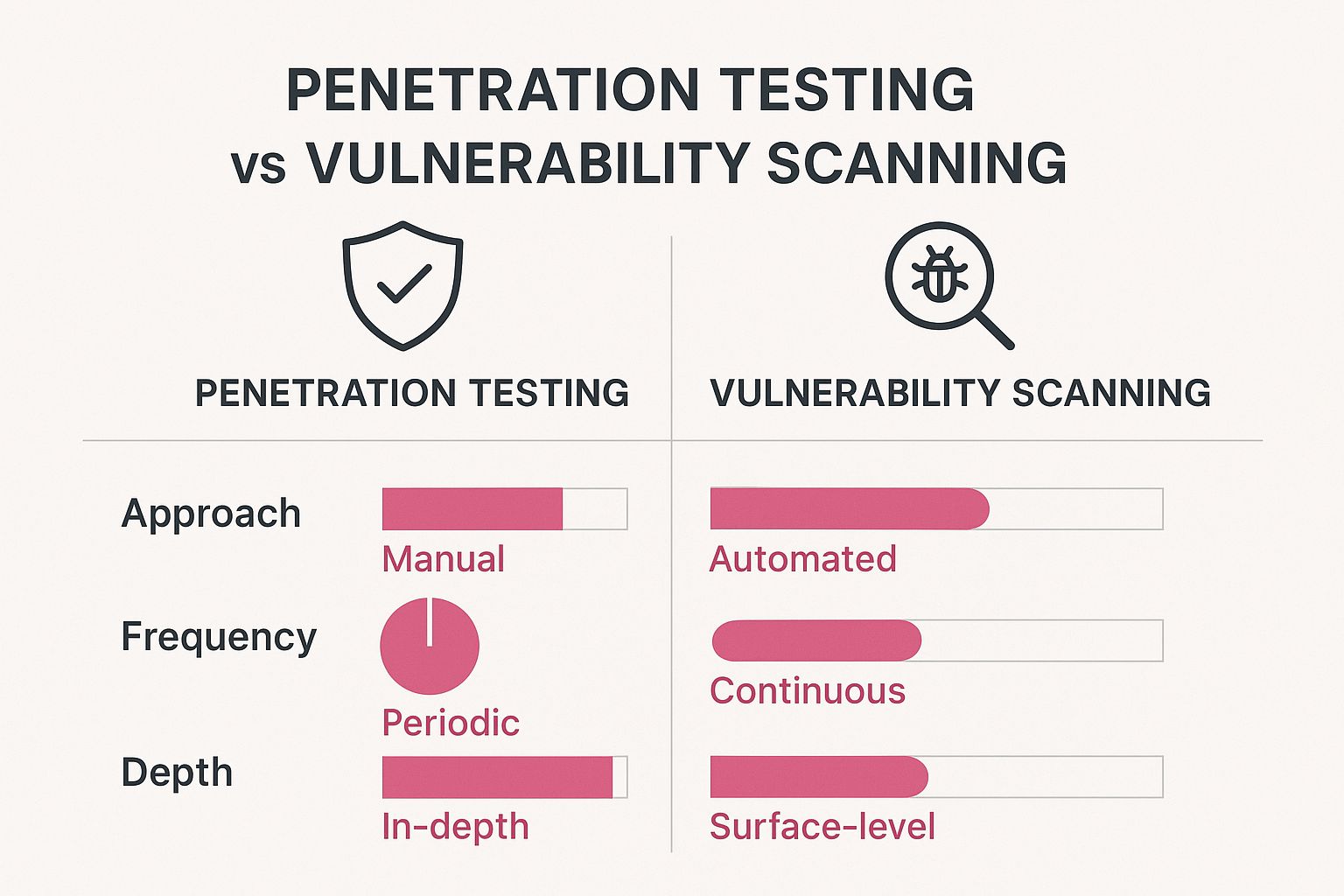
Let's break down exactly what sets them apart.
Methodology: Automated vs Human-Led
The most significant difference lies in how each assessment is performed. Vulnerability scanning is a purely automated process. It uses specialised software to systematically check your networks, servers, and applications against a huge, constantly updated database of known security flaws. It is fast, efficient, and great for broad coverage.
Penetration testing, on the other hand, is a human-led, manual process. It leans on the expertise, creativity, and intuition of a seasoned ethical hacker simulating a genuine attack. Pen testers use automated tools, of course, but their real value is their ability to think like an adversary, connect seemingly minor issues into a major breach, and adapt their attack in real-time. That is something no automated scanner can do.
Objective: Find vs Exploit
Their core goals are also worlds apart. A vulnerability scan is designed to find and catalogue potential weaknesses. It gives you an inventory of problems, usually prioritised by a generic severity score, but it stops there. It does not actually try to see if these flaws can be used against you.
A penetration test has a much more direct objective: to actively exploit those vulnerabilities to understand their real-world impact. The entire point is to prove whether a theoretical risk can be turned into a concrete security incident, like gaining access to sensitive customer data or taking control of a critical system.
A vulnerability scan tells you a door has a standard lock that's known to be pickable. A penetration test actually picks the lock, walks inside, and shows you exactly what a burglar could steal.
This distinction is absolutely vital when it comes to deciding what to fix first. A 'critical' finding from a scan might be a false positive or mitigated by other controls. A successful exploit in a pen test report is undeniable proof of a clear and present danger that needs immediate attention.
Scope And Depth
Vulnerability scans are built for breadth. They can assess thousands of devices across your entire network in a relatively short time, giving you a wide but somewhat shallow overview of your overall security hygiene. They answer the question, "What potential issues do we have across our entire estate?"
Penetration testing is all about depth. It focuses on a much narrower, pre-agreed scope—like a single web application or the company’s crown jewels—and dives deep. The goal is to uncover complex, multi-stage attack paths that an automated tool would miss entirely. It answers the more pressing question, "How vulnerable are our most important assets to a determined attacker?"
To put these differences into a clearer context, let's look at a direct feature comparison.
Vulnerability Scanning vs Penetration Testing Feature Comparison
The following table breaks down the key distinctions across several critical business and technical criteria, offering a clear snapshot of where each approach excels.
| Criterion | Vulnerability Scanning | Penetration Testing |
|---|---|---|
| Primary Method | Automated software scans | Manual, human-driven expertise |
| Core Goal | Identify a broad list of known vulnerabilities | Exploit vulnerabilities to prove real-world impact |
| Scope | Wide and shallow (entire networks) | Narrow and deep (specific applications/systems) |
| Speed | Fast (hours to days) | Slower (days to weeks) |
| Cost | Lower, often subscription-based | Higher, project-based investment |
| Key Output | Long list of potential flaws with severity scores | Detailed narrative report of exploits and business risk |
| Human Element | Minimal human involvement | Relies entirely on an expert's skill and creativity |
| Best For | Routine security hygiene, broad compliance checks | Verifying security controls, assessing business risk |
This table clearly shows that you are not choosing one over the other, but rather deciding which one is right for a specific purpose at a specific time.
Reporting And Output
Nowhere are the differences more obvious than in the final reports. The output from a vulnerability scanner is essentially a long, technical list of everything it found.
- Vulnerability Scan Example Output: 'Potential SQL injection vulnerability identified on login page (CVE-2023-XXXX). CVSS Score: 9.8 (Critical).'
This is useful for a technical team, but it lacks business context. It does not confirm if the flaw is truly exploitable in your environment or what the damage would be.
A penetration test report, however, tells a story. It details the steps the ethical hacker took, the vulnerabilities they successfully exploited, and, most importantly, the business impact.
- Penetration Test Example Output: 'We successfully exploited an SQL injection vulnerability on the main login page. This allowed us to bypass authentication and gain administrative access to the customer database, from which we exfiltrated 5,000 customer records, demonstrating a critical risk to business operations and GDPR compliance.'
This kind of detail is far more compelling for business leaders. It directly connects a technical flaw to a tangible risk to the organisation’s reputation and bottom line, making it much easier to justify the resources needed for remediation.
When Should You Use Each Security Method?
Understanding the difference between penetration testing and vulnerability scanning is one thing, but knowing the right time to use each is what really builds a strong security posture. These two methods are not interchangeable. They serve different purposes and address specific risks, so choosing the right one for the situation is fundamental to a smart cyber defence strategy.
For most UK businesses, the choice often comes down to compliance needs, your tolerance for risk, and whether you are going through major operational changes. Each approach gives you a different kind of reassurance, so matching the assessment to your business context is vital to get the most value from your investment.
When to Rely on Vulnerability Scanning
Think of vulnerability scanning as your regular, ongoing security check-up. Its automated nature makes it ideal for frequent scans that help you maintain a solid baseline of security across your entire organisation. It is the broad-strokes approach you need to catch common misconfigurations and missing patches before they escalate into serious problems.
Consider using vulnerability scanning in these common scenarios:
- Meeting Routine Compliance: For certifications like the basic Cyber Essentials, regular vulnerability scans are a must-have to prove you are keeping systems patched and configured correctly.
- Continuous Monitoring During Development: If your team is constantly shipping new code, integrating automated scans into your development pipeline is a practical way to spot common vulnerabilities before a product goes live. For instance, a scan can automatically check new code for known insecure libraries.
- Maintaining an Asset Inventory: Regular scanning helps you keep a clear picture of all the devices and software on your network, quickly flagging anything unauthorised or out-of-date that could pose a risk. A weekly scan, for example, could reveal a new, unmanaged server has been connected to the network by a developer, creating a security blind spot.
When a Penetration Test is Essential
A penetration test, on the other hand, is for moments that demand a much deeper, more rigorous level of assurance. It is a strategic investment you make to see if your defences can actually hold up against a skilled, determined attacker, especially during critical business moments or when you are responsible for highly sensitive data. It answers the crucial question: "Are our most important assets really secure?"
A penetration test is the right call in these situations:
- Before a New Application Launch: Before you push a new customer-facing web application or a major software update live, a pen test is essential to find hidden business logic flaws that automated tools miss. For example, a tester could discover a way to manipulate prices in an e-commerce checkout process.
- After Major Infrastructure Changes: Just finished a big cloud migration or a complete network redesign? A pen test confirms that the new setup has been configured securely from the ground up, verifying that complex cloud permissions have not accidentally exposed sensitive data.
- Satisfying Stringent Regulations: Compliance frameworks like PCI DSS do not just recommend penetration testing—they require it regularly to prove that cardholder data is protected against real-world attack techniques.
- Providing Investor or Client Assurance: If you are preparing for a funding round or pitching for a major new contract, a clean penetration test report offers concrete proof that you take security seriously, demonstrating due diligence to stakeholders.
A common mistake is thinking automated scans are enough. The latest Cyber Security Breaches Survey found that while 67% of medium and 74% of large UK businesses suffered a breach, many still rely on scans that simply cannot detect complex, multi-stage attacks. A penetration test simulates these advanced threats, giving you the real-world intelligence needed to fix what matters most.
Ultimately, you need a balanced approach. Vulnerability scans provide the steady, continuous rhythm of security maintenance. Penetration tests deliver the periodic, deep-dive validation required to defend against sophisticated threats. Understanding the various cyber security threats managed services can shield your business from can also help put this layered defence into a broader context.
Understanding Costs And ROI In The UK Market
When you start comparing penetration testing and vulnerability scanning, one of the most immediate and stark differences is the cost. It is not just a small gap; the financial investment for each reflects a fundamental split in methodology, depth, and the human expertise involved. For any UK business trying to budget for security, getting your head around these financial aspects is absolutely essential.

Vulnerability scanning is, by a long shot, the more affordable of the two. It is usually sold as a Software-as-a-Service (SaaS) product, which means you are looking at a predictable monthly or yearly subscription. This model is great because it gives you continuous, automated scanning without a hefty upfront cost, making it a really accessible way to maintain basic security hygiene.
Penetration testing, on the other hand, is a different beast entirely and commands a much higher price tag. Why? Because you are not just buying software. You are investing in the time, skill, and creative thinking of certified security professionals. Their hands-on, intelligence-led approach takes days, sometimes weeks, of intensive work, and that is what the cost reflects.
Demystifying UK Pricing Structures
Looking at the UK market, the pricing data shows a clear divide. A professional penetration test could set you back anywhere from a few thousand pounds to upwards of £20,000, all depending on the scope and complexity of the job. A typical day rate for a manual tester sits somewhere between £1,000 and £1,500.
A word of caution: if you see a service advertised for less than £500 a day, you should be asking some serious questions. At that price point, it is almost certainly not a true manual test and likely involves very little hands-on work.
This is a critical pitfall for businesses. Many low-cost services are marketed as ‘pen tests’ but are, in reality, just repackaged vulnerability scans with a quick manual once-over. These services simply do not have the depth to find complex, chained vulnerabilities, and relying on them can create a dangerous false sense of security.
Be wary of any penetration test that seems suspiciously cheap. True penetration testing is a specialist skill, and its price reflects the value of discovering critical, business-ending flaws before a real attacker does.
Focusing On Return On Investment
While a pen test costs more at the outset, its real return on investment (ROI) comes from risk reduction. Consider a practical example: a pen test costs £5,000 but discovers a flaw that, if exploited, could lead to a £50,000 regulatory fine and significant reputational damage. The ROI is immediately apparent. A good pen test directly tackles these massive financial risks by finding and helping you fix exploitable flaws.
Ultimately, the goal is to match your security spending to your risk profile. A smart, layered security programme uses both: vulnerability scanning for continuous, broad monitoring and penetration testing for deep, periodic dives. This combined approach ensures you are not just managing your security posture, but also keeping a firm grip on your IT assets. For a deeper look into that, consider reading our guide on what IT asset management is and why it's important.
Frequently Asked Questions
When it comes to cybersecurity, it is natural for business leaders to have questions. One of the most common areas of confusion is the difference between penetration testing and vulnerability scanning, and knowing which one you need is crucial for making smart security investments. Here are some straightforward answers to the queries we hear most often.
We have shaped these answers around the practical, real-world concerns of UK businesses, aiming to clear up any lingering uncertainty.
Do I Need Both Penetration Testing and Vulnerability Scanning?
In short, yes. For a truly robust security strategy, you absolutely need both. They are not an either/or choice; they are two sides of the same coin, tackling security from different, complementary angles. Vulnerability scanning gives you the continuous, broad-brush overview you need to catch known issues and maintain good cyber hygiene.
Think of it as your day-to-day security baseline. A penetration test, on the other hand, provides the deep, periodic dive required to uncover complex weaknesses and confirm if those vulnerabilities could actually be exploited by a real attacker. One gives you breadth, the other gives you depth. Together, they create a powerful, layered defence.
How Often Should My Business Conduct a Penetration Test?
For most UK businesses, an annual penetration test is the recommended minimum. This frequency ensures your defences are properly scrutinised against the ever-changing threat landscape at least once a year.
However, you should not just stick to a rigid 12-month schedule. It is vital to commission a new test after any significant changes to your IT environment.
Key triggers for an additional test include:
- Launching a new, business-critical application.
- Moving to a new cloud provider or completing a major cloud migration.
- Rolling out substantial updates to your infrastructure or software.
- Meeting specific compliance needs, as some standards like PCI DSS mandate more frequent testing.
Can a Penetration Test Cause Downtime for My Systems?
This is a perfectly valid concern, but a professionally conducted penetration test is carefully planned to minimise any risk of business interruption. Reputable ethical hackers operate under strict, pre-agreed rules of engagement that clearly define the scope and what is off-limits. For instance, they might agree to only perform resource-intensive tests outside of core business hours.
They use controlled techniques designed to prove a vulnerability exists without causing system instability or crashes. While there is always a tiny inherent risk with live testing, close communication between the testing team and your technical staff ensures business continuity is the top priority.
The goal of a professional penetration test is to simulate an attack's outcome, not its collateral damage. Testers aim to demonstrate risk safely and responsibly, providing actionable intelligence without disrupting your operations. This focus on controlled, non-disruptive testing is a hallmark of a reputable provider.
Is Vulnerability Scanning Enough for Cyber Essentials Certification?
It depends entirely on which level of the UK's Cyber Essentials certification you are aiming for. For the foundational Cyber Essentials certificate, regular vulnerability scanning is a core requirement and is generally sufficient. It helps find problems like unpatched systems and basic configuration errors that the scheme focuses on.
However, for the more advanced Cyber Essentials Plus certification, vulnerability scanning alone will not cut it. This higher tier requires a hands-on technical audit by an external assessor. This process involves techniques much closer to penetration testing to verify that potential vulnerabilities cannot actually be exploited, providing a much stronger guarantee of your security.
At SES Computers, we understand that building a resilient security posture requires a strategic blend of tools and expertise. Our managed services provide the proactive monitoring and vulnerability management your business needs to stay ahead of threats. Contact us today to discuss a tailored security solution.